
Oliver Page
Case study
December 8, 2025

Cybersecurity Compliance vs. Best Practice: What Schools Are Actually Required to Do in 2026 comes down to understanding the difference between meeting minimum legal obligations and building a truly resilient defense against evolving threats.
Quick Answer: What's Required vs. What's Recommended
Federal Laws
Staff Training
Access Control
Vendor Management
Incident Response
As we approach 2026, K-12 schools face a dramatically different cybersecurity landscape than even a few years ago. Cyberattacks on educational institutions have surged, with hackers leveraging AI-powered phishing, deepfake scams, and ransomware-as-a-service to target districts of all sizes. The December 2024 PowerSchool breach, which exposed student data from thousands of schools, served as a wake-up call for the entire sector.
At the same time, the regulatory environment has grown more complex. While federal laws like FERPA have been around for decades, state-level privacy legislation has exploded since 2014, with nearly 400 student privacy bills introduced across 49 states. By 2026, districts must steer a patchwork of mandates—from New York's Education Law 2-d requiring specific vendor contracts, to Texas SB 820 mandating cybersecurity policies, to California's CCPA imposing annual audits on larger EdTech vendors.
Here's the critical insight many IT directors miss: meeting compliance requirements is just the starting line, not the finish line. Compliance tells you the legal minimum to avoid fines or loss of funding. Best practices tell you what actually works to protect your students, staff, and operations from real-world threats.
The gap between these two approaches has never been wider—or more dangerous to ignore.
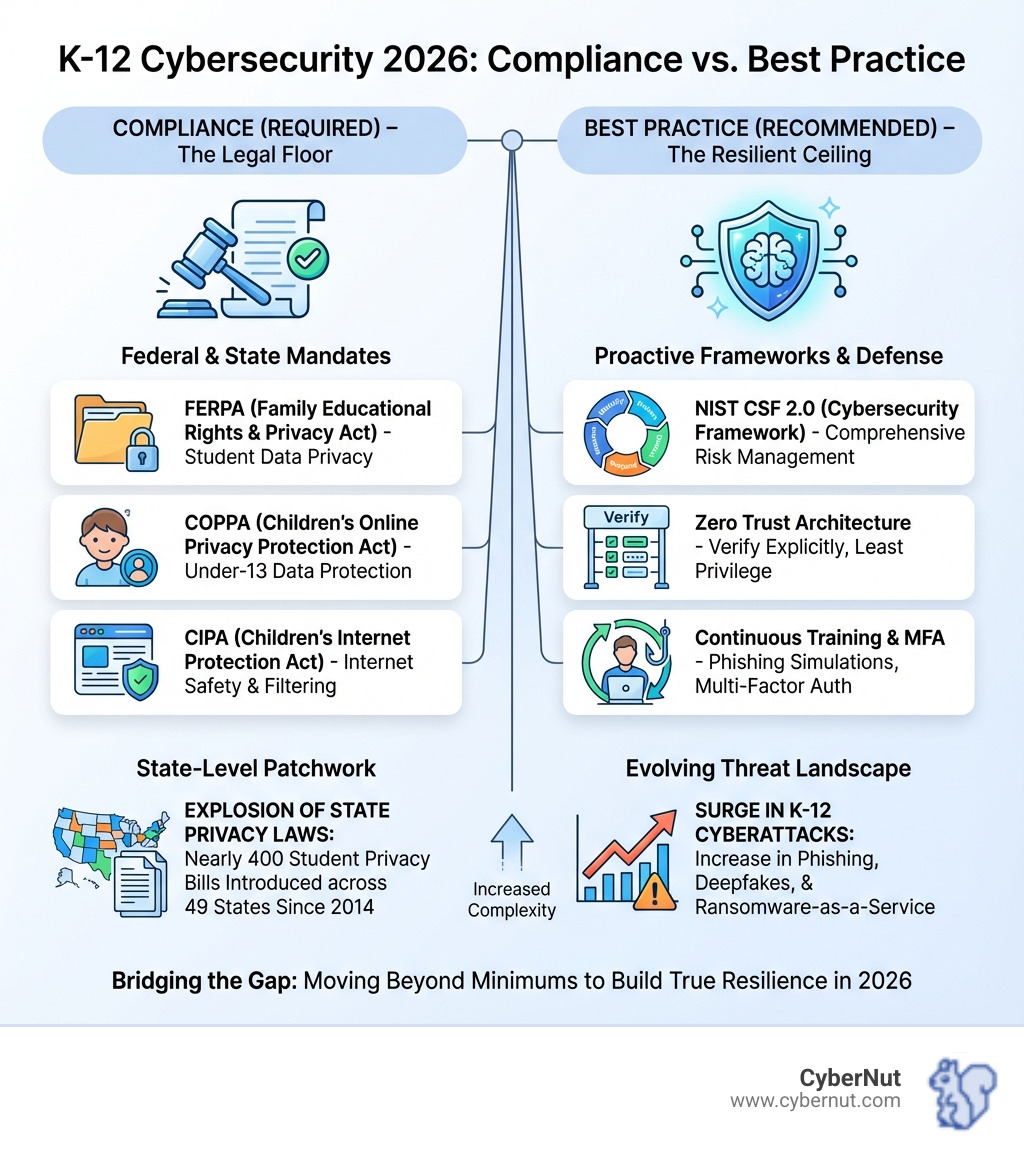
When we talk about Cybersecurity Compliance vs. Best Practice: What Schools Are Actually Required to Do in 2026, the "required" part forms our compliance floor. This floor is built on a foundation of federal and state laws, defining the non-negotiable minimums for protecting student data and school systems. Failing to meet these mandates can lead to severe consequences, including hefty fines, loss of funding, and significant reputational damage.

At the federal level, three key laws anchor student data privacy and security:
FERPA (Family Educational Rights and Privacy Act): This foundational law governs the privacy of student education records. While FERPA doesn't explicitly mandate specific technical cybersecurity controls, it implicitly requires schools to take "appropriate steps" to safeguard student records from unauthorized disclosure and misuse. Without robust security, the risk of FERPA violations, and the resulting identity theft or fraud for students, escalates dramatically. The "school official exception" allows third-party vendors to access student data under certain conditions, but only if they are under the school's direct control and use data solely for educational purposes, reinforcing the need for strict vendor agreements. For a deeper dive, read our article, All About FERPA: The Federal Student Privacy Law That Still Matters in 2025.
COPPA (Children's Online Privacy Protection Act): COPPA focuses on protecting the online privacy of children under 13. It requires websites and online services to obtain verifiable parental consent before collecting, using, or disclosing personal information from these younger children. This is particularly relevant for EdTech tools used in elementary and middle schools. Our research shows that The Children's Online Privacy Protection Act (COPPA) will continue to be a critical compliance component.
CIPA (Children's Internet Protection Act): CIPA requires schools and libraries receiving E-Rate discounts for internet access or internal connections to implement internet safety policies. These policies must include technology protection measures to block or filter internet access to obscene, child pornography, or harmful content for minors. While less about data privacy, CIPA is a key federal compliance requirement tied to crucial funding.
Beyond federal mandates, schools in 2026 face an increasingly complex "patchwork" of state-specific privacy laws. Since 2014, nearly 400 student privacy bills have been introduced across 49 states, as highlighted by the Student Privacy Compass' Guide to State Laws. This trend signifies a national movement towards stronger protections, but it also creates a significant compliance challenge for schools operating across state lines or using nationally available EdTech.
Examples include:
New York's Education Law 2-d: This law, explained in detail in our blog All About New York's Education Law 2-D: Student Data Privacy Explained, imposes stringent requirements on schools and their third-party vendors regarding the protection of personally identifiable information (PII). It often mandates specific contract clauses and alignment with frameworks like NIST CSF.
California's SOPIPA and CCPA: California has been a leader in data privacy. SOPIPA (Student Online Personal Information Protection Act) specifically restricts how EdTech vendors can use student data, preventing targeted advertising and profile building. The CCPA (California Consumer Privacy Act), for its part, impacts larger EdTech vendors and, by 2026, will mandate annual cybersecurity audits for larger companies, with potential fines up to $7,500 per violation. Learn more with our guide, What to Know About the California Consumer Privacy Act (CCPA) for Schools.
Texas SB 820: This law, discussed in All About Texas SB 820: Cybersecurity Policies Required in Every School District, requires every school district to adopt a cybersecurity policy, emphasizing the state's commitment to securing educational systems.
These state laws often define specific breach notification timelines (e.g., 72 hours to the district, 14 days to parents), data deletion policies, and requirements for vendor contracts, making them critical components of compliance.
Schools increasingly rely on EdTech vendors for everything from learning management systems to student information platforms. However, this reliance introduces significant third-party risk. As our research notes, "attackers frequently target vendors and supply chains to exploit vulnerabilities in weaker links." The PowerSchool breach, which impacted numerous K-12 institutions, is a stark reminder of these risks, prompting K-12 leaders to scrutinize vendor security.
By 2026, managing third-party vendor risk is not just a best practice; it's a critical compliance requirement. Schools must ensure that every vendor handling student data adheres to strict privacy and security standards. This means:
Failure to properly manage vendor risk can result in fines (e.g., CCPA penalties), loss of federal or state funding, and severe damage to a school's reputation.
Understanding the distinction between compliance and best practices is paramount for schools in 2026. Compliance is about meeting the baseline, avoiding penalties, and demonstrating due diligence. Best practice, however, is about building genuine resilience, proactively managing risk, and ensuring operational continuity regardless of the threat landscape.

Let's expand on our quick answer to highlight this crucial difference across key cybersecurity areas:
The cyber threat landscape is evolving at a terrifying pace. By 2026, attackers are more sophisticated, often leveraging advanced technologies that compliance minimums simply can't keep up with:
The PowerSchool data breach, which was a "stark reminder of these risks," highlighted how even seemingly secure systems can have weak links. As Powerschool Breach Reveals Weak Links demonstrates, relying solely on compliance can leave schools vulnerable to these advanced threats.
The answer to Cybersecurity Compliance vs. Best Practice: What Schools Are Actually Required to Do in 2026 is multifaceted. Schools are legally obligated to meet compliance requirements to avoid penalties, maintain funding, and demonstrate due diligence. This is the floor. However, best practices represent an ethical responsibility to genuinely protect students, staff, and operations. They are essential for ensuring student safety, maintaining operational continuity, and building trust with the community. While compliance is a checklist, best practice is a continuous journey towards resilience.
Moving beyond the compliance floor, building a best-practice security program is about creating a holistic, layered defense that can withstand evolving threats. This doesn't necessarily mean breaking the bank; it's about smart, scalable solutions and a strategic approach to risk management.
Frameworks provide a structured approach to cybersecurity, helping schools assess their posture and identify areas for improvement.
NIST CSF 2.0: The National Institute of Standards and Technology (NIST) Cybersecurity Framework 2.0, unveiled in 2024, is its most significant update. It extends its reach beyond critical infrastructure to include a wider array of organizations, "including small schools, nonprofits, large agencies, and corporations, regardless of their cybersecurity expertise." This makes it an ideal, flexible guide for educational institutions. The framework now encompasses six core functions: Identify, Protect, Detect, Respond, Recover, and Govern. The new "Govern" function emphasizes cybersecurity's role in enterprise risk management, a critical shift for school leadership. The NIST Cybersecurity Framework was established in response to an executive order by former President Obama — Improving Critical Infrastructure Cybersecurity — and has become a gold standard.
Zero Trust Architecture (ZTA): As our research highlights, "the days of trusting your internal network simply because it sits behind a firewall are over. In 2026, Zero Trust Architecture (ZTA) has become the gold standard for securing business systems. The principle is simple but powerful: trust nothing, verify everything." This means every user, device, and application must be authenticated and authorized before gaining access, regardless of whether they are inside or outside the traditional network perimeter. Key components include least privilege access and mandatory Multi-Factor Authentication (MFA) across all systems.
While not strictly required, adopting these frameworks can significantly improve a school's security posture and often helps meet specific compliance requirements more efficiently. Other useful frameworks for third-party assurance include ISO 27001, considered the "international cybersecurity standard," and SOC 2, for verifying secure management of client data.
Our research consistently shows that "human error remains the #1 cause of cyber incidents." Even the most advanced technical controls can be bypassed by a single click on a malicious link. This is why the "human firewall" – your staff and students – is arguably the most critical component of a robust security program.
Even with the best defenses, breaches can happen. That's why having a tested and effective incident response and recovery plan is essential. Our research states, "even the most secure systems can be breached. That’s why having a tested incident response (IRP) plan is essential."
We understand that budget constraints are a significant reality for many schools. While it might seem daunting, even small or rural districts can make substantial improvements. The key is prioritization and leveraging available resources. Focus on high-impact basics first, such as mandatory MFA, basic security awareness training, and robust endpoint protection.
Federal grants, like the K-12 Cybersecurity Readiness Grant Program, can provide much-needed funding. Additionally, many districts benefit from shared services organizations (e.g., BOCES or ESAs) that pool resources and expertise. Our article, Small IT Teams, Big Security Stakes: Lessons from Rural K-12 Districts, offers valuable insights for these situations.
There's no single "silver bullet" in cybersecurity; a layered defense is always best. However, if we had to pick the most impactful investments, it would be a combination:
These two investments address critical attack vectors and provide a strong return on investment by preventing many common breaches.
If a third-party vendor experiences a data breach involving your school's data, your responsibilities are primarily dictated by your contractual agreements with the vendor and state-specific breach notification laws. Your contract should include clear breach notification clauses, requiring the vendor to notify your district immediately (e.g., within 72 hours).
Your district is then typically responsible for notifying affected parents and students, adhering to specific state laws regarding notification timelines and procedures. Failure to comply can result in significant legal and reputational consequences. For more details, consult our guide, Third-Party Data Breaches 101.
As we've explored, Cybersecurity Compliance vs. Best Practice: What Schools Are Actually Required to Do in 2026 clearly positions compliance as the essential starting line. It's the bare minimum required to avoid penalties and maintain operational legitimacy. However, the rapidly evolving threat landscape—marked by AI-powered attacks and sophisticated social engineering—demands that schools strive far beyond this floor. Best practices are not luxuries; they are necessities for building genuine resilience and ensuring the safety and privacy of our students and staff.
Building a proactive security culture, fostering continuous improvement, and securing strong leadership buy-in are paramount. At CyberNut, we believe a strong human firewall, empowered by effective training, is the most cost-effective and powerful defense for any school. To see how vulnerable your district is to the #1 threat vector, get a free phishing audit and start building a more resilient security culture today.

Oliver Page

Some more Insigths


Back