
Oliver Page
Case study
August 8, 2025

All About Texas SB 820: Cybersecurity Policies Required in Every School District - here's what every K-12 IT director needs to know:
Quick Overview:
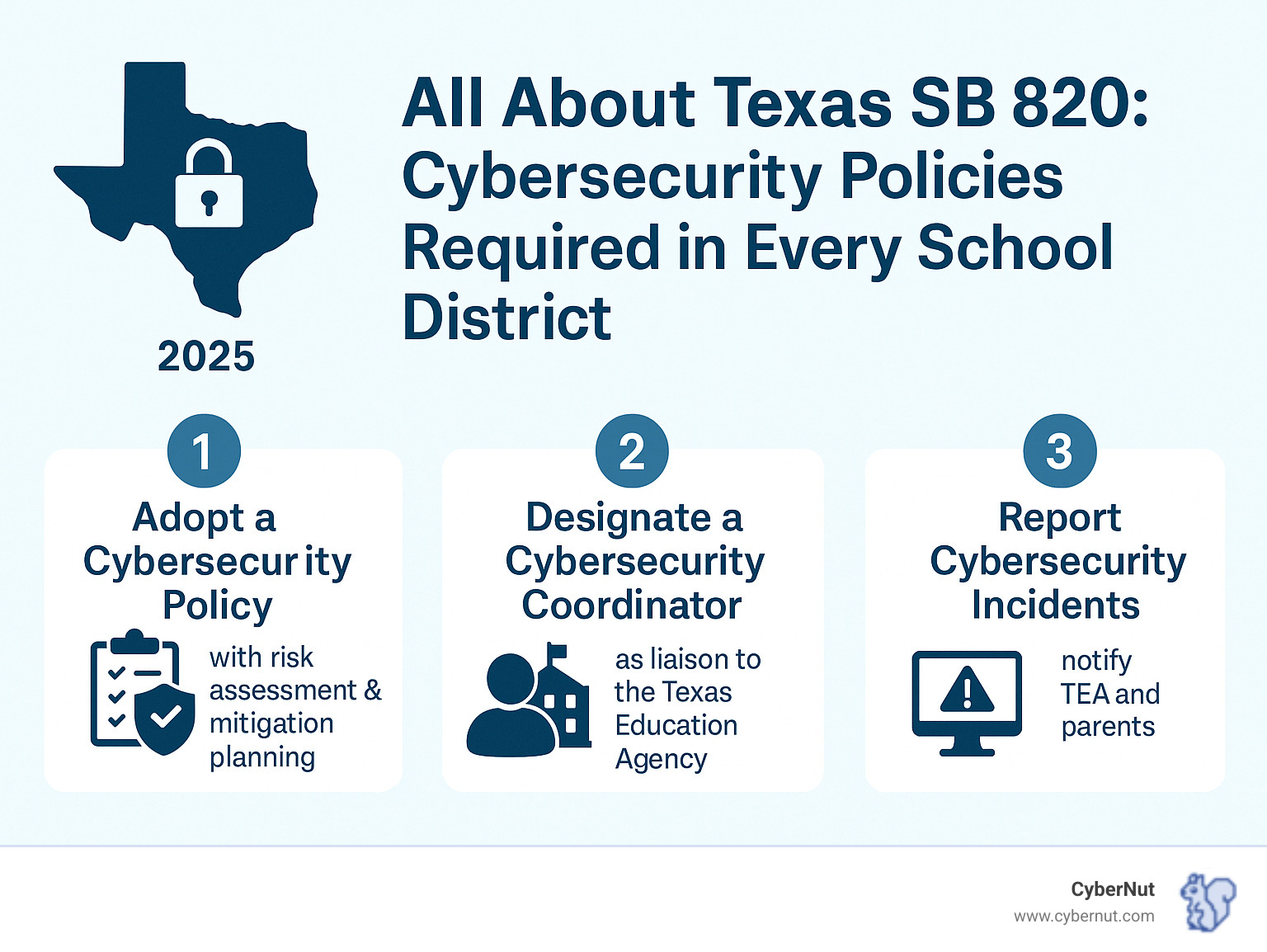
The Three Mandatory Pillars:
The numbers tell a sobering story. Cybersecurity incidents at K-12 schools have increased by 30 percent, and schools now face a 92% spike in cyberattacks compared to previous years. The educational services sector experienced 1,780 cyber incidents in 2023 alone, with 1,537 involving confirmed data disclosure.
Recognizing this escalating threat, Texas lawmakers passed SB 820 as a proactive measure to protect sensitive student data, including personally identifiable information (PII), health records, and individualized education plans (IEPs).
For stretched IT directors, SB 820 may seem like another hurdle. However, it's more than a legal requirement; it's a framework for building a resilient cybersecurity foundation to protect students, staff, and the district's reputation.
The law aligns with the Texas Cybersecurity Framework, offering clear guidance on risk assessment and mitigation. While mandatory, it allows districts flexibility in how they implement their policies.
Effective September 1, 2019, All About Texas SB 820: Cybersecurity Policies Required in Every School District was a direct response to a harsh reality: schools had become prime targets in the digital world.
Districts hold a goldmine of sensitive data, from student records to staff information. Cybercriminals noticed this, and with fewer security resources, schools became the second most targeted industry for cyberattacks. The pandemic expanded the attack surface with remote learning, creating new vulnerabilities that Texas lawmakers acted decisively to address.

SB 820's three core requirements are powerful: adopt a comprehensive cybersecurity policy, designate a cybersecurity coordinator to liaise with the Texas Education Agency (TEA), and report breaches to the TEA and affected parents.
Compliance offers benefits beyond avoiding legal trouble. It builds stronger defenses, protects student data, and earns community trust. However, implementation has challenges, including resource constraints and complex risk assessments. Proper planning is key, and robust Incident Response Planning in K12 is essential to turn compliance into a strategic advantage.
A cybersecurity policy under SB 820 is a strategic roadmap for protecting your district's digital assets and sensitive data. The law requires the policy to secure cyberinfrastructure, include risk determination and mitigation plans, and not conflict with state information security standards for higher education.
Your policy should include procedures for risk assessment, mitigation strategies, incident response planning, data classification, access control, employee training, and vendor management. Aligning your policy with the Texas Cybersecurity Framework (TCF) is key. The TCF mirrors the NIST Cybersecurity Framework's five functions: Identify, Protect, Detect, Respond, and Recover. Following the TCF means adopting best practices that offer flexibility while aligning with the state's vision.
The cybersecurity coordinator, designated by the superintendent, is the critical link between your district and the TEA on all cybersecurity matters. Their responsibilities extend beyond basic IT support.
As the TEA liaison, they handle all state cybersecurity communication, including reports and threat responses. They must report any cyberattack or breach to TEA "as soon as practicable." Another crucial duty is parent notification for incidents involving student data, which helps maintain trust.
The coordinator also oversees policy implementation, ensuring all departments follow protocols. They often lead risk management, including threat identification, vulnerability assessment, and developing mitigation strategies. This role lifts cybersecurity to a strategic priority, expanding IT staff responsibilities and often requiring new skills.
For districts looking to strengthen their security posture, exploring Cybersecurity Audits: Strengthening K-12 Schools Against Cyber Threats can provide valuable insights.
SB 820 clearly defines a "breach of system security" as any incident where sensitive, protected, or confidential student information is stolen, copied, transmitted, viewed, or used by unauthorized individuals.
In case of a breach, the cybersecurity coordinator has a dual reporting duty. First, they must report to TEA "as soon as practicable." This reporting helps TEA understand statewide threats and offer assistance. The Texas Department of Information Resources also maintains a cybersecurity incident response hotline.
Second, the coordinator must notify parents or guardians of affected students. This transparency allows families to take precautions if their child's data is at risk. These requirements show the state's commitment to protecting student personally identifiable information (PII), ensuring privacy is protected with clear accountability.
Swift, transparent reporting helps maintain community trust. For detailed guidance, districts can reference School Cybersecurity: Security Breach Notification and Response.
Translating All About Texas SB 820: Cybersecurity Policies Required in Every School District from mandate to practice requires a clear strategy. The real work is implementing these requirements across your organization.
SB 820 impacts all IT infrastructure and staff. IT departments are on the front lines, securing networks, managing devices, and responding to sophisticated threats. This shift requires re-evaluating systems and investing in new technologies like multi-factor authentication, robust monitoring tools, and end-to-end encryption.
It's not just about technology. Staff responsibilities also expand. All staff must participate in cybersecurity training and follow new protocols. While challenging, this is an opportunity. Districts that accept this change are better prepared for evolving threats. Mitigating Cybersecurity Risks: Protecting K-12 Schools from Evolving Threats is a continuous effort that strengthens the organization.
Risk assessment is the foundation of an effective SB 820 policy. It's like mapping your digital territory to plot a safe course.
The NIST Framework is an invaluable guide, as the Texas Cybersecurity Framework follows its principles. NIST's five core functions (Identify, Protect, Detect, Respond, Recover) provide a comprehensive roadmap for compliance and for developing your RFP for Cybersecurity.
At its core, SB 820 safeguards sensitive student data, including personally identifiable information (PII), protected health information (PHI), and Individualized Education Program (IEP) data. It protects this data by mandating comprehensive policies, risk assessments, and mitigation plans, encouraging practices like strong access controls and data encryption.
SB 820 works alongside federal laws like FERPA (Family Educational Rights and Privacy Act). FERPA governs the privacy of student records, focusing on rights to access and control how data is shared. SB 820 complements FERPA by mandating the technical safeguards to protect that data from cyberattacks. While FERPA sets rules for who can access data, SB 820 builds the digital fortress around it. This comprehensive approach builds family trust by ensuring student data receives the utmost protection.
Both SB 820 and HB 3834 strengthen cybersecurity for Texas schools, but they tackle different parts of the puzzle. They are complementary forces working toward the same goal.
SB 820 focuses on policy and structure, forming the foundation of your cybersecurity program. HB 3834 addresses the human element with mandatory, annual DIR-certified User Training: Pillar in Cybersecurity for School Districts. It recognizes that technical safeguards fail without trained users.
The bottom line: you need both. Policy without training is incomplete, and training without policy lacks direction. Together, they create a robust defense against K-12 threats.
Navigating new cybersecurity legislation can be overwhelming. Here are answers to common questions about All About Texas SB 820: Cybersecurity Policies Required in Every School District.
While SB 820 doesn't specify fines, the real-world consequences of non-compliance can be devastating:
The potential for a state audit is just the tip of the iceberg compared to these consequences.
You're not alone. Texas offers a robust support network to help districts with implementation:
No, SB 820 does not apply to charter schools. The legislation targets public school districts, and the TEA has clarified that open-enrollment charter schools are not required to comply with SB 820 or HB 3834.
However, charter schools should still consider adopting similar practices. They handle the same sensitive data and face the same cyber threats. Many charters voluntarily implement similar policies as a good business practice to protect students, maintain trust, and reduce risk. For these schools, SB 820 resources can still provide excellent guidance for building a strong cybersecurity foundation.
All About Texas SB 820: Cybersecurity Policies Required in Every School District is more than a compliance checkbox; it's a roadmap to a secure educational environment. It lifts cybersecurity from an IT task to a district-wide priority.
SB 820 pushes districts toward a proactive security posture, providing a framework for strategic planning and building defenses before an attack occurs. This requires building a culture of cybersecurity where protection is everyone's job. When all staff understand their role in spotting threats and handling data securely, real security is achieved.
This cultural shift requires ongoing, engaging training. Traditional training is often seen as a chore, but interactive and relevant content leads to better retention. Phishing awareness is critical as it's the top attack vector for schools. Cybercriminals target busy educators, making targeted, engaging training essential for your security posture.
At CyberNut, we know the right training transforms a district's security culture. Our automated, gamified micro-trainings are designed for K-12 schools. We offer bite-sized, engaging content that fits into busy educator schedules.
The combination of SB 820 compliance and effective staff training creates a powerful defense system. Your policy provides the framework, your coordinator ensures oversight, and your trained staff serve as your first line of defense against threats.
Ready to see where your district stands against one of the most common cyber threats? Get a free phishing audit for your district and find exactly how vulnerable your staff might be to these attacks.
When you're ready to transform compliance from a burden into a competitive advantage, explore CyberNut's K-12 Cybersecurity Solutions. Let's work together to build not just a compliant district, but a truly secure one that protects what matters most - your students' data and their educational future.

Oliver Page

Some more Insigths


Back