
Oliver Page
Case study
November 17, 2025

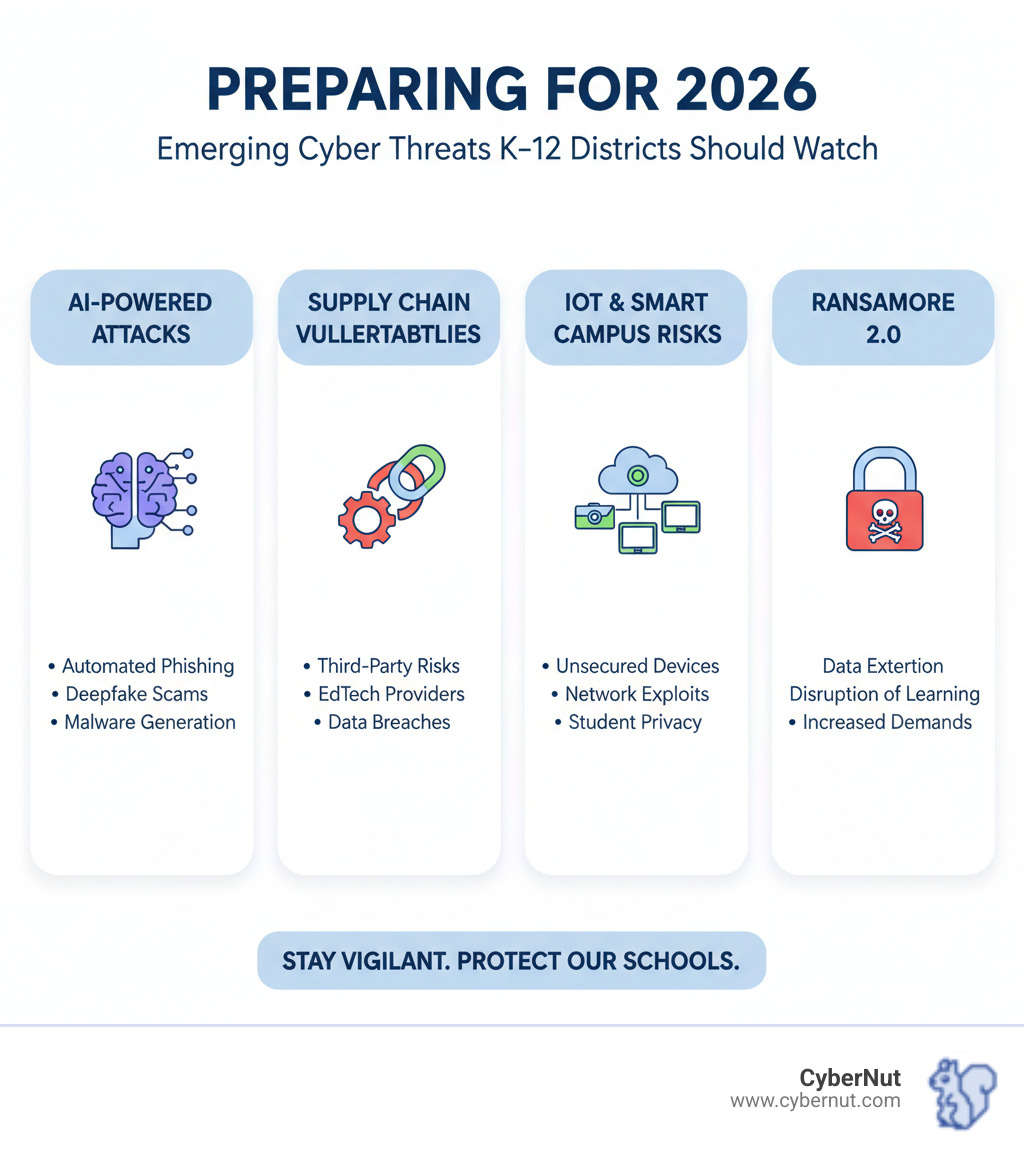
Preparing for 2026: Emerging Cyber Threats Every K–12 District Should Watch is critical as schools face unprecedented cyber attacks. With 82% of K-12 institutions reporting cyber threat impacts and recovery costs ranging from $50,000 to over $9 million, the days of simple firewalls are gone. The threat landscape has been reprogrammed by AI, internal risks, and complex supply chains.
Top Emerging Cyber Threats for 2026:
The financial and educational impact is staggering. Beyond multi-million dollar losses, schools lose precious learning time. The reality is that K-12 schools are "target-rich and cyber-poor," holding vast amounts of student data but often lacking dedicated cybersecurity budgets.
As one IT leader noted, "When I presented the statistics on daily attacks to district leaders, eyes went wide—people didn't realize the scale of what we face every day."
This guide moves beyond generic warnings to show you specific threats and practical solutions, helping you build a "human firewall" that turns staff and students into your strongest defense.
Ready to see where your district stands? Get a free phishing audit to identify your most critical vulnerabilities.
Preparing for 2026: Emerging Cyber Threats Every K–12 District Should Watch terms to remember:

The world of cyber threats is changing at lightning speed. For K-12 districts, Preparing for 2026: Emerging Cyber Threats Every K–12 District Should Watch is essential for survival. Let's explore the sophisticated threats that will be knocking on our digital doors.
For cybercriminals, AI is rocket fuel. It helps them create phishing attempts that are faster, more accurate, and more convincing than ever. Imagine an email from your superintendent that looks perfect—no typos, no awkward grammar. That's AI helping bad actors craft messages that are nearly impossible to distinguish from the real thing. They can also create pixel-perfect fake login pages to trick staff and students.
AI also automates credential attacks and enables MFA fatigue, where users are spammed with authentication requests until they accidentally approve one. It's no wonder 70% of administrators believe AI is increasing cybersecurity risks. To see how well your district can spot these clever new phishing attempts, claim a free, no-obligation phishing audit from CyberNut today.
Ransomware has evolved from simply locking files to a much nastier threat. Ransomware-as-a-Service (RaaS) makes it easy for more criminals to launch attacks. We're also seeing double and triple extortion: attackers first steal your data, then threaten to publish it online. They may add more pressure by launching attacks to shut down your website.
The results are heartbreaking. Students can lose anywhere from 3 days to 3 weeks of learning time. Recovery can take 2 to 9 months, with costs soaring from $50,000 to over $1 million. The attack on Baltimore County Public Schools cost over $9.5 million, while New Haven Public Schools lost $6 million. Protecting against these attacks requires strong defenses and smart strategies.
Often, the weakest link in our cybersecurity chain isn't our own network but our third-party vendors, cloud services, and hardware providers. If a student information system or transportation app is breached, that single compromise can impact dozens of districts. It's crucial to:
The risk isn't always from the outside. We're seeing a 29% surge in student-to-student security incidents, from cyberbullying to account takeovers. Accidental data exposure from misconfigured file-sharing or unencrypted documents is also a major risk. While less common, malicious insider activity from a disgruntled staff member or student remains a possibility.
These internal risks highlight the need to protect student accounts, which are increasingly prime targets. In fact, 1 in 4 school systems report a rise in cyberattacks aimed at student accounts, showing that everyone in the school community has a role in cybersecurity.

Understanding Preparing for 2026: Emerging Cyber Threats Every K–12 District Should Watch means understanding why your school is such an attractive target. Cybercriminals deliberately choose K-12 districts because of their valuable assets and systemic vulnerabilities.
The phrase "target-rich, cyber-poor" perfectly captures the problem. Schools hold a goldmine of sensitive data: student Social Security numbers, home addresses, health records, and Individualized Education Programs (IEPs). This is the personally identifiable information (PII) that criminals crave.
Yet, 61% of school districts rely on general funds rather than dedicated cybersecurity budgets. This often means understaffed IT departments, outdated equipment, and a reactive approach to security. Cybercriminals know this, making schools an appealing target with a high effort-to-reward ratio. It's no surprise that 82% of reporting K-12 schools have already experienced cyber threat impacts.
The rapid shift to 1:1 device programs, remote learning, and cloud services has dramatically expanded your attack surface. Every Chromebook, tablet, and IoT device—from smartboards to security cameras—is a potential entry point.
Your reliance on cloud services like Google Workspace and Microsoft 365 is also a key factor. A single misconfigured sharing setting can expose vast amounts of data. Meanwhile, many districts wrestle with legacy systems and unpatched software due to budget constraints. This mix of old and new technology creates an environment where vulnerabilities can easily slip through the cracks.
Perhaps the most alarming vulnerability is the "student security gap." While 90% of teachers and 95% of IT staff have multi-factor authentication (MFA) protection, only 5% of students do. This massive disparity creates a gaping hole in your defenses.
This matters because 1 in 4 school systems now report increased cyberattacks specifically targeting student accounts. A compromised student account can be used to launch phishing campaigns against staff, access other students' data, or pivot deeper into school systems. Students often lack awareness of cybersecurity best practices, making them more likely to use weak passwords or fall for social engineering. Closing this student security gap is essential for shoring up your entire district's defenses.
Curious about where your district's most critical vulnerabilities lie? A free phishing audit can help you identify exactly which users and accounts are most at risk.
The evolving threat landscape makes one thing clear: building a resilient defense is not optional. The good news is that Preparing for 2026: Emerging Cyber Threats Every K–12 District Should Watch doesn't require unlimited budgets. It requires smart, strategic thinking and a commitment to foundational security practices.
Certain cybersecurity measures are non-negotiable, regardless of budget. These are the absolute foundation for every K-12 district.
Beyond the foundation, districts need a layered defense model. Frameworks like the K12 SIX Essential Cybersecurity Protections and the NIST Cybersecurity Framework provide excellent guidance.
Endpoint Detection and Response (EDR) solutions give you eyes on every device, monitoring for suspicious activity. Zero Trust principles shift the security mindset to "never trust, always verify," requiring every user and device to prove their identity for every access request. Adopting industry-standard frameworks from organizations like K12 SIX and the Center for Internet Security (CIS) provides a proven roadmap. Finally, AI is also a powerful ally in defense, automating threat detection and response when integrated into existing security tools.
With 61% of districts relying on general funds, smart budgeting is key. Leveraging federal and state programs is one of the best moves you can make. In June 2024, the FCC announced a $200 million cybersecurity pilot program under E-Rate, helping schools afford necessary tools. Districts can apply for this funding by completing FCC Form 484.
Exploring grants from state and private organizations should be an ongoing effort. Collaborating with neighboring districts to share expertise and services multiplies everyone's resources. Finally, maximize existing tools by enabling all available security features, reviewing cloud platform settings, and tuning alerts to focus on critical threats. Many powerful security features are already paid for but not activated.
Want to see where your district's vulnerabilities actually lie? Get a free phishing audit to identify your most critical gaps.
You can have the most advanced technology, but if a staff member clicks a convincing phishing link, all those defenses can crumble. Building a "human firewall" is essential. When Preparing for 2026: Emerging Cyber Threats Every K–12 District Should Watch, we must remember that our strongest defense is a culture where everyone understands their role in protecting the district.
Traditional, boring cybersecurity training doesn't work. We need continuous, engaging learning that builds security habits. As one expert said, "When a suspicious email lands, I want them to see my face before they click."
If you're wondering where to focus your training efforts, a free phishing audit can show you exactly where your weak points are.
Your district relies on dozens of EdTech vendors and cloud platforms, each a potential entry point. You must vet vendors thoroughly by asking hard questions about their security certifications and incident response plans. Reviewing data sharing agreements is also crucial to know exactly how your data is being handled. Finally, conduct ongoing monitoring of cloud app permissions in platforms like Google Workspace and Microsoft 365, as misconfigured settings are a common source of data exposure. CyberNut offers a FREE Google Workspace and/or Microsoft 365 Security & Safety Audit to help identify these vulnerabilities.
You are not alone in this fight. Some of the most effective security improvements come from collaboration.
Collaboration is essential. The threats are too sophisticated for any district to handle in isolation. By building strong partnerships, you create a resilient defense that can adapt and grow.
Understanding the rules and having a solid plan for when things go wrong are key to Preparing for 2026: Emerging Cyber Threats Every K–12 District Should Watch. Let's break down the essentials of compliance and crisis management.
The laws designed to protect student data are evolving rapidly. In 2023 alone, 33 states passed 75 new cybersecurity laws for education, covering everything from data sharing to incident reporting. You may have seen this in your state with new rules like the GaDOE Cybersecurity Guidelines for K–12 Districts, Massachusetts’ 201 CMR 17.00, or Illinois’ Data Breach Law.
While federal laws like FERPA set the baseline, new state laws often add stronger protections and mandate swift incident reporting. On the funding front, the FCC's $200 million E-Rate Cybersecurity Pilot Program is a huge step to help schools afford security upgrades. The bottom line: you must be able to prove your district is actively securing student data.
It's not a question of if your district will face a cyber incident, but when. A clear, step-by-step playbook is essential. A robust incident response plan, following guidance from the NIST Computer Security Incident Handling Guide, includes these key steps:
Crucially, your plan must include clear communication strategies for staff, students, parents, and law enforcement to prevent chaos and misinformation during a crisis. The Anonymized Threat Response Guidance: A Toolkit for K-12 Schools provides a helpful framework for this.
It's natural to have questions when navigating the complex world of K-12 cybersecurity. Here are concise answers to some of the most common ones as you focus on Preparing for 2026: Emerging Cyber Threats Every K–12 District Should Watch.
There are two equally critical first steps. First, develop and test a comprehensive incident response plan so you know exactly how to act during a crisis. Second, implement Multi-Factor Authentication (MFA) for all users, especially students. With only 5% of students protected by MFA, their accounts are prime targets. Closing this "student security gap" is one of the most effective defenses against account takeovers.
Even with a tight budget, you can make huge strides. Start by leveraging free resources from organizations like K12 SIX and CISA. Focus on maximizing the tools you already own by enabling MFA and tightening sharing settings in cloud platforms. Actively seek funding through programs like the FCC's E-Rate Cybersecurity Pilot Program and state-level grants. Finally, collaborate with neighboring districts to share costs, expertise, and services.
Effective training builds a "human firewall" through engagement, not boredom. Ditch long, annual presentations for short, regular, and relevant micro-trainings. Use gamified lessons and realistic phishing simulations to build practical habits, like pausing before clicking a link. The goal is to make security second nature through consistent, positive reinforcement, not to cause training fatigue. As one IT leader said, "You don't need new tools to teach someone to pause before they click."
Want to see how well your human firewall is performing? Get a free, no-obligation phishing audit from CyberNut to identify your district's specific vulnerabilities.
The journey toward Preparing for 2026: Emerging Cyber Threats Every K–12 District Should Watch can feel daunting. We've covered AI-powered phishing, advanced ransomware, and the critical student security gap. The threats are formidable, but they are not impossible to overcome.
The shift from a reactive to a resilient cybersecurity posture requires a multi-layered strategy combining modern technology, smart budgeting, and robust collaboration. It means embracing AI as both a threat and a defense, understanding your district's unique vulnerabilities, and leveraging every available resource.
Most importantly, it requires building a strong "human firewall." Technology alone is not enough. The best firewall can't stop a person from clicking a convincing phishing link. True resilience is achieved when your staff instinctively pauses before clicking, when students understand the risks of weak passwords, and when everyone sees cybersecurity as a shared responsibility.
By taking proactive steps now—implementing MFA for all, creating a tested incident response plan, and investing in continuous, engaging training—your district can safeguard its data and ensure the continuity of learning.
CyberNut specializes in creating that human firewall through automated, gamified training designed specifically for the K-12 environment. Our approach is about building security habits that stick, without overwhelming your busy staff and students.
Ready to see where your district stands? Get a free, no-obligation phishing audit to identify your most critical vulnerabilities. For more strategies and guidance on building your resilient defense, explore our comprehensive cybersecurity resources.
The threats are evolving, but so are the solutions. Your district's journey from reactive to resilient starts today.

Oliver Page

Some more Insigths


Back