
Oliver Page
Case study
December 3, 2025

Opsec & Appsec: Application Security Emerges As New Focus describes a critical shift in how organizations protect their digital assets. As applications become more complex and central to operations, security priorities are moving from traditional operational security (Opsec) to application security (Appsec). Artificial intelligence is accelerating this change.
The numbers are stark: eight of the top 10 data breaches in 2023 stemmed from application vulnerabilities. With 71% of organizations deploying updates at least weekly, the attack surface is constantly expanding. Traditional security, with its periodic manual tests and slow reviews, can no longer keep up.
Appsec addresses the reality that software now drives revenue and user experience in every sector, including education. By integrating security into the development process (DevSecOps) and leveraging AI, organizations can automate vulnerability detection and achieve continuous security validation, making digital platforms safer and more resilient.

Software is everywhere, from the apps on our phones to the learning platforms in schools. Modern applications are no longer simple, monolithic programs. They are complex ecosystems of microservices, APIs, and cloud-native technologies spread across multiple environments. Each connection point is a potential entry for attackers, and traditional Application Security Testing (AST) tools struggle to keep up.
A major issue is the false positive problem. Many older Static Application Security Testing (SAST) tools generate so much noise that developers begin to ignore alerts, leading to alert fatigue. This wastes valuable time and makes it harder to spot real threats. For K-12 schools on tight budgets, investing in tools that create confusion is not a viable option.
Another challenge is the architecture mismatch. Tools designed for monolithic applications are ill-equipped to analyze the distributed nature of modern cloud-native apps. They can't follow API calls across services or handle newer frameworks, leaving significant security blind spots. When critical vulnerabilities like Log4Shell emerge, the slow response time of outdated tools leaves organizations dangerously exposed.
The solution is DevSecOps, a cultural shift that integrates security into every stage of the development lifecycle. This practice, known as "shifting left," addresses security concerns early in the process. Finding and fixing a vulnerability during development is dramatically cheaper and faster than fixing it in a live production environment.
DevSecOps relies on automated AST tools to improve efficiency and provide continuous feedback. This automation frees security professionals to focus on strategic challenges rather than repetitive scans. The benefits are clear: higher developer efficiency, improved security coverage, and reduced remediation costs. For schools adopting new educational technologies, this means safer applications without slowing down innovation.
Traditional security testing methods are falling behind. Key limitations include:
These limitations underscore why Opsec & Appsec: Application Security Emerges As New Focus is a necessary evolution. We need security approaches as dynamic as the applications they are built to protect.
Artificial Intelligence is reshaping offensive security by providing speed and scale that human teams cannot match alone. AI-powered systems work 24/7, processing vast amounts of data to identify vulnerabilities. This enables a shift from periodic penetration testing to continuous security validation, where problems are caught as they emerge.
AI excels at pattern recognition and anomaly detection, spotting subtle irregularities that might evade human analysts. AI-driven vulnerability scanners don't just find issues; they prioritize them based on real-world exploitability, allowing teams to focus on the greatest risks. For K-12 schools with limited resources, this provides access to enterprise-level protection without the need for a large security operations center.
Traditional threat modeling is static and quickly becomes outdated. AI-driven threat modeling is dynamic and intelligent. AI systems can run adaptive attack simulations that alter tactics mid-simulation based on what they encounter, such as network defenses or real-time environmental changes. It's like sparring with an opponent who learns and adapts to your moves.
This adaptive approach provides an authentic view of an organization's security posture, showing how defenses hold up against an evolving adversary. The difference between continuous validation and periodic pentesting is like having a 24/7 security guard versus one who only visits every few months.
Many security tasks, like reconnaissance and password cracking, are tedious and time-consuming. AI automates these routine jobs, freeing up human experts to focus on strategic tasks that require creativity and critical judgment. Instead of manual data collection, security professionals can analyze complex attack scenarios and design more resilient architectures.
This shift toward proactive defense strengthening offers a significant strategic advantage, allowing teams to anticipate threats rather than constantly reacting to them. The reality is that Opsec & Appsec: Application Security Emerges As New Focus because AI makes it possible to secure complex application environments efficiently and effectively.
Moving from traditional to AI-improved security is like switching from a once-a-year photo to a 24/7 security camera. The difference in visibility and responsiveness is immense.
Traditional security relies on manual effort and static analysis, which is slow and misses novel threats. Its periodic nature means that a security assessment is outdated almost as soon as it's completed. This approach is human-led and does not scale to meet the demands of modern, rapidly changing environments.
AI-improved approaches flip this model. Automation handles the repetitive work, while dynamic and adaptive analysis allows the system to learn and respond in real-time, just like a real attacker. This enables continuous testing, where security validation never stops. For K-12 schools managing sensitive data across complex digital platforms, this constant vigilance is invaluable.
Moving beyond point-in-time pentesting is a major advantage of AI. Continuous security validation is an always-on assessment that provides real-time visibility into your defenses. AI tools run simulations 24/7, probing for weaknesses and validating that security controls work as intended.
This approach means you are constantly simulating evolving threats, incorporating new threat intelligence as it emerges. The result is a real-time security posture that reflects your actual defensive capabilities now, not months ago. This transforms security from a periodic checkbox exercise into an ongoing process of strengthening risk and resilience. To understand your current human security layer, consider starting with a comprehensive phishing audit.
While AI offers incredible promise for Opsec & Appsec: Application Security Emerges As New Focus, it's not a magic bullet. Adopting AI requires managing a new set of risks, including AI model security, data quality, and ethical dilemmas. Awareness of these challenges is the first step toward using AI safely and effectively.
An AI is only as smart as the data it's trained on. This is the "garbage in, garbage out" problem. Incomplete, outdated, or biased training data will create blind spots in your AI model that attackers can exploit. The AI might simulate unrealistic attacks, giving a false sense of security, or miss critical vulnerabilities entirely. The solution is to prioritize a continuous pipeline of high-quality, diverse, and current threat data to train and retrain your models.
Ironically, the AI tools used to find vulnerabilities can themselves be vulnerable. Attackers can use adversarial attacks to trick AI systems. Evasion attacks can make malicious code appear harmless to an AI scanner, while poisoning attacks corrupt the AI's training data from the start, fundamentally flawing its learning process. Defending against these attacks requires treating AI models as critical assets, using techniques like adversarial training, and continuously monitoring model integrity.
As AI in offensive security becomes more powerful, it raises complex ethical and legal questions. The potential for misuse is a major concern; a powerful security tool could become a powerful attack tool in the wrong hands. The legal boundaries of automated, simulated attacks can be murky, especially when they interact with third-party systems.
For educational institutions, data privacy concerns are paramount. AI models need data, but that data may be subject to privacy laws like FERPA. Furthermore, the "black box" nature of some AI models raises issues of transparency and accountability. Organizations must establish clear ethical frameworks, governance policies, and human oversight before deploying AI-driven security tools to ensure they are used responsibly. To see where your organization stands, consider starting with a phishing audit.
Adopting AI into your security operations requires a strategic approach. To succeed with Opsec & Appsec: Application Security Emerges As New Focus, organizations should follow several best practices.
AI will not replace security teams. It acts as a force multiplier, handling repetitive, data-intensive tasks at a scale humans cannot. This frees up security professionals to focus on what they do best: strategic thinking, creative problem-solving, and interpreting complex results. Human intuition and experience are irreplaceable when facing novel threats or making nuanced risk assessments. The most effective security posture comes from combining AI's automation with the judgment of skilled professionals, especially in resource-constrained environments like K-12 schools.
If you're ready to strengthen your organization's security foundation, a great first step is to understand your current vulnerabilities. Consider starting with a comprehensive phishing audit.
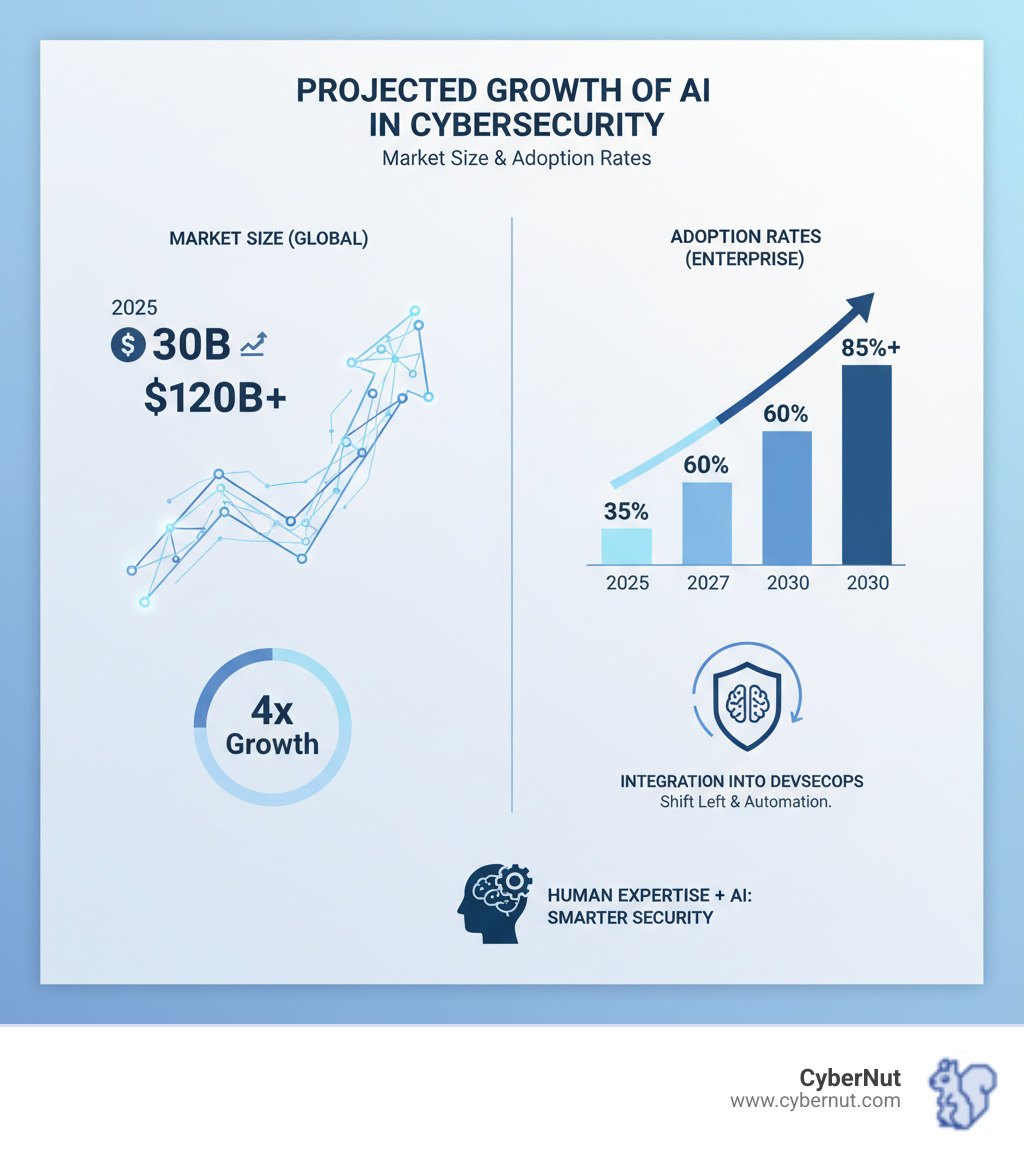
The future of Opsec & Appsec: Application Security Emerges As New Focus is being shaped by AI, leading to a fundamental shift from reactive to proactive defense. We are moving toward a world where security systems can predict and neutralize threats before they materialize.
Future advancements include:
These advancements are leveling the playing field, making sophisticated defenses accessible to organizations of all sizes, including K-12 schools that often operate with limited IT resources.
In practice, we will see the rise of highly realistic AI-driven red teams that can simulate complex, multi-stage attacks and adapt their tactics on the fly. Autonomous security agents will not just find problems but actively solve them by suggesting or even implementing fixes.
This evolution will not eliminate cybersecurity jobs but transform them. As AI handles repetitive tasks, the demand for human expertise in AI governance, strategic security planning, and threat hunting will grow. Roles like Security Engineers, Architects, and CISOs will focus on leveraging AI strategically and providing critical human oversight. The cybersecurity talent shortage will persist, but AI will make each professional more effective. For K-12 schools, AI-powered tools combined with proper training, like the cybersecurity awareness programs CyberNut provides, can significantly improve security without requiring a large dedicated team.
The future is a partnership between technology and humanity. To see where your organization stands today, get a phishing audit to assess your human defenses.
It's clear that Opsec & Appsec: Application Security Emerges As New Focus is a necessary evolution in cybersecurity. As applications become the backbone of our schools and businesses, traditional security methods are no longer sufficient. The speed of modern development and the complexity of today's threats demand a more dynamic, integrated, and continuous approach.
AI is the game-changer that makes this possible. It provides the speed and scale for continuous security validation, adapts to mimic real-world attackers, and automates tedious tasks. However, AI is a tool, not a panacea. It requires high-quality data, protection from adversarial attacks, and responsible ethical governance.
The most resilient organizations will be those that blend AI's power with indispensable human expertise. This combination creates a security posture that is both intelligent and wise, automated and strategic. For K-12 schools, building this resilience starts with a strong security culture, where every teacher, administrator, and student understands their role in protecting sensitive data.
At CyberNut, we help educational institutions build that culture. Our gamified, automated micro-trainings make cybersecurity awareness engaging and effective.
Ready to take the first step? Understanding your current vulnerabilities is key. To improve your organization's resilience, start with a comprehensive phishing audit to see where your defenses stand today. From there, you can learn more about building a strong security culture with cybersecurity training designed for the unique needs of K-12 schools.

Oliver Page

Some more Insigths


Back