
Oliver Page
Case study
August 11, 2025

Texas HB 3834 Explained: The Law That Mandates Cybersecurity Training for Educators is a law requiring annual cybersecurity awareness training for school district and local government employees across Texas. Here's what you need to know:
The reality is stark: Texas faced over 10,000 attempted cyberattacks per minute in January 2020, according to the Department of Information Resources. In August 2019, more than 20 local governments reported ransomware attacks that forced them offline.
School districts are prime targets because they hold vast amounts of sensitive student data, from academic records to health information. Every email account is a potential entry point for cybercriminals looking to deploy ransomware or steal personal information.
HB 3834, passed by the 86th Texas Legislature, recognizes that people are both the weakest link and the strongest defense in cybersecurity. The law creates a "human firewall" by ensuring educators can recognize and respond to cyber threats.
For K-12 IT Directors, this means navigating new compliance requirements while improving your district's security posture. The good news is you have flexibility in choosing training that works for your staff.

Texas HB 3834 is fundamentally about building a stronger defense against cyber threats. Passed by the 86th Texas Legislature, this law recognizes a simple truth: your people are your best protection against hackers and cybercriminals.
The law's core purpose is to create a "human firewall." Instead of relying solely on technology, HB 3834 ensures that everyone with access to government computer systems knows how to spot and stop cyber threats before they cause damage.
The legal foundation is in Texas Government Code 2054.519, which sets the framework for how Texas manages its information resources. The law covers state and local government employees, school district staff, elected officials, and even contractors with access to government systems.
For schools, the law defines "access" simply. If you have an account to log into any local government computer system or database, you're covered. This means having a school email address or district system login likely makes the law apply to you.
There's an important distinction: for state agencies, employees typically need training only if they use computers for at least 25% of their job duties. For local governments and school districts, however, the 25% computer use rule doesn't apply. If you have system access, you are potentially subject to the training requirement, regardless of how much time you spend on a computer.
This makes sense, as a teacher who only checks email twice a day is just as vulnerable to a phishing attack as someone who works on a computer all day. One wrong click can lead to a ransomware attack that shuts down your entire district.
The training requirements under HB 3834 apply to nearly everyone working with government computer systems. Local government employees are the largest group, including city hall workers and school district staff. If they can log into a government system, they're likely covered.
Elected officials like school board members must complete the training if they have system access. The same applies to appointed officials who use computers for at least 25% of their duties and have system access.
For school district staff, while only the cybersecurity coordinator is legally required to complete training, districts can require it for anyone with system access. Since phishing emails don't discriminate, most experts recommend training everyone with an email account.
Contractors with system access to state agencies must also complete certified training, though this applies specifically to state-level, not local government, contractors.
For school districts, the law requires a cybersecurity coordinator who must complete annual training. This person acts as your district's cybersecurity champion, responsible for understanding threats and protecting your school community.
The key flexibility is that districts decide, in consultation with their cybersecurity coordinator, who else needs training. The law empowers you to identify which employees need training based on their access levels and risk.
This is crucial because school districts hold sensitive data like student records, health information, and personal details, making them attractive targets. A successful attack costs money and can damage the trust between families and schools for years.
The smart approach is to train anyone with an email account or system access. It only takes one successful phishing email to compromise your network. When protecting sensitive student data, it's better to be cautious.
Ready to see how effective training can transform your staff into cyber defenders? Explore our insights on Cybersecurity Training Empowering K-12 Staff Against Cyber Threats.

Think of the Texas Department of Information Resources (DIR) as the quality control center for Texas HB 3834. Working with the Texas Cybersecurity Council, DIR ensures that available training programs are effective in protecting your schools.
DIR has three key responsibilities: certifying at least five training programs annually to provide choice, developing specific criteria for these programs, and maintaining an updated list of certified options on their website for easy access.
The certification criteria are practical. Programs must focus on forming information security habits and procedures that protect your school's digital resources. This is about building everyday habits, not just memorizing jargon.
The second requirement is that training must teach best practices for detecting, assessing, reporting, and addressing information security threats. Your staff needs to know what a phishing email looks like, how to spot potential malware, and who to contact when something seems off, as a quick response is critical.
Finding the right training program is straightforward. DIR maintains a comprehensive list of certified programs that meet all state requirements on its cybersecurity awareness training certification webpage. This page is your starting point for ensuring compliance and includes FAQs, updates, and the list of certified programs.
For budget-conscious districts, DIR offers a free certified training program. Their training videos are available in English and Spanish. The trade-off is that you must handle tracking completion internally, as the free version lacks automated reporting or certificates.
When evaluating paid programs, consider what matters most to your district. All certified programs meet DIR's core requirements, but they differ in delivery, engagement, and reporting. Some focus heavily on phishing awareness—a top attack vector—while others take a broader approach.
If phishing is a major concern, you might explore specialized training. We have more info about a Phishing Awareness Training Program that shows how targeted training can improve your district's security culture.
The key is finding a program your staff will engage with, not just click through for a certificate. The goal isn't just compliance—it's creating a school where everyone can confidently spot and stop cyber threats.

Think of Texas HB 3834 compliance as your district's annual cybersecurity health check-up. Staying on top of these requirements keeps your digital defenses strong.
The most important date is August 31st, the annual compliance reporting deadline for DIR. This predictable date simplifies planning.
You have flexibility in tracking completion internally. DIR doesn't mandate specific software; you can use spreadsheets, HR systems, or other tools. For a streamlined option, DIR's Texas by Texas (TxT) tool allows employee self-reporting and provides verification reports.
Your governing board holds the ultimate responsibility for ensuring compliance and conducting periodic audits to make sure the district meets its training obligations.
Understanding the annual cycle helps you plan ahead. The process begins with training providers, not your district.
From June 1 to July 31, training companies submit programs to DIR for certification. These certifications are valid until August 31 and must be renewed annually, ensuring you always have fresh training options.
Throughout the year, your employees must complete their certified cybersecurity training. There is no single statewide deadline for finishing the training itself, giving you room to schedule it when it works best for your staff.
The August 31st compliance reporting deadline is when you certify to DIR that your required personnel have completed their training.
Reporting compliance is straightforward. You'll use DIR's Cybersecurity Training Certification for State and Local Governments form to submit your certification.
Any individual authorized by your school district can handle the submission, not just the cybersecurity coordinator. This could be someone from administration, HR, or IT. They will need access to their email to confirm the submission with a verification code.
Importantly, DIR doesn't want individual training records or employee certificates. Your job is to keep those records internally for your own documentation and potential audits. The state trusts you to maintain accurate records.
Your governing board must verify and report on training completion. While DIR provides a Governing Board Acknowledgement Form for internal use, you are not required to submit it. This gives your district flexibility to document compliance in a way that works for your board.
While Texas HB 3834 casts a wide net, some practical exceptions exist. Employees on extended leave (e.g., military, FMLA) without system access are typically exempt during their absence.
An interesting exception exists for districts with robust internal programs. If your school employs a dedicated information resources cybersecurity officer, you might qualify for a certification exception. This means your internal training program doesn't need DIR's stamp of approval, as long as it covers the required content. You must still submit this exception to DIR annually, but it offers more flexibility.
Now, what happens if you don't comply? HB 3834 doesn't include direct financial penalties for school districts. However, the law requires periodic audits to ensure compliance. Documented non-compliance can lead to negative audit findings, reputational damage, and scrutiny from state authorities.
The real consequence is far more immediate: increased security risks. Without proper training, your staff is vulnerable to sophisticated cyberattacks like phishing and ransomware. The financial and operational damage from a successful attack will likely far exceed any theoretical penalties.
HB 3834 works alongside SB 820, another Texas law focused on school cybersecurity. While HB 3834 addresses the human element via training, SB 820 requires districts to develop comprehensive cybersecurity policies, including risk assessment and mitigation plans. Together, they form a solid foundation for district protection.
Want to see how well your current training is working? Consider testing your staff with an AI Phishing Simulator for Teachers & Staff to identify areas that need attention.
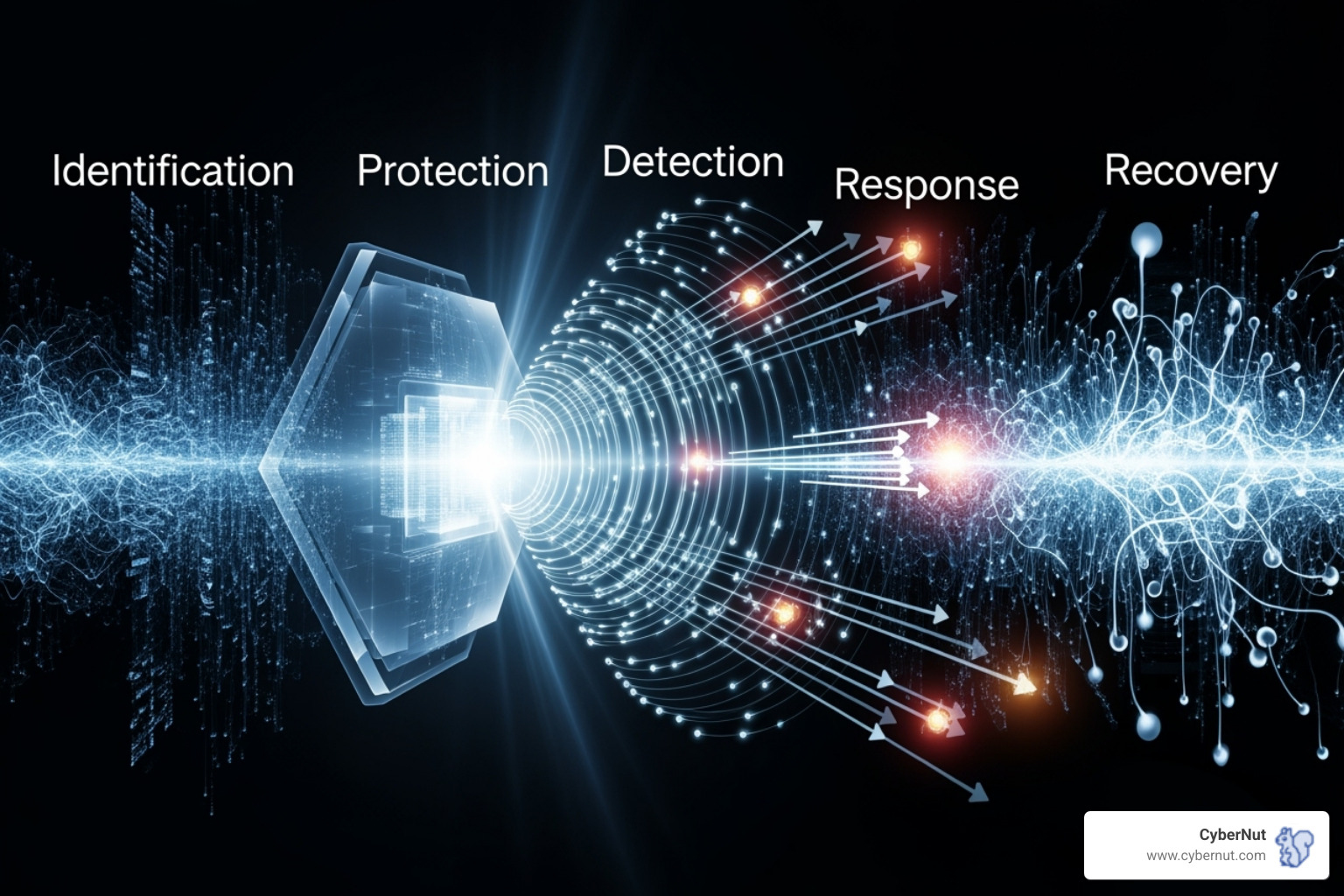
The Texas Cybersecurity Framework (TCF) is the state's guiding strategy for cybersecurity, and HB 3834's training requirements are one piece of this larger picture.
The TCF is a self-assessment tool to help organizations understand risks and measure their maturity. It's built on five functions: Identify assets and vulnerabilities, Protect critical services, Detect incidents, Respond effectively, and Recover quickly.
For state agencies and universities, the TCF is a mandatory standard. School districts have more flexibility. While you must comply with HB 3834 and SB 820, you can follow other frameworks like NIST or CIS RAM, provided they don't conflict with the TCF.
However, DIR and TEA often reference the TCF, making it a practical choice for many districts. It provides a systematic way to identify vulnerabilities and implement controls beyond just staff training.
The TCF promotes a holistic view of cybersecurity, from data inventory to incident recovery planning. It's the difference between simply playing defense and having a complete game plan.
If you want to dive deeper into how the TCF works, check out these helpful presentation slides for the Texas Cybersecurity Framework that break down its complexities.
Navigating new legislation can be overwhelming. Here are answers to common questions about Texas HB 3834.
The answer hinges on one key word: access. Texas HB 3834 requires training for anyone with access to a local government computer system or database. If part-time staff or substitutes have a school email account or system login, they are technically covered.
While the Cybersecurity Coordinator has the discretion to determine training frequency for most employees, best practice is to include everyone with system access. Cybercriminals don't care if someone works 10 hours a week or 40; every email account is a potential entry point for an attack.
Phishing attacks don't discriminate. A substitute teacher's account is just as vulnerable as a full-time employee's. One wrong click can put your entire network at risk. Therefore, training anyone with an email address or system login is the safest approach to protecting student data.
The law is specific about the required content. DIR mandates two main focus areas to build a human firewall.
First, training must focus on forming information security habits and procedures to protect your school's information resources. This means building practical, everyday habits like using strong passwords, recognizing suspicious emails, and handling sensitive data properly.
Second, training must teach best practices for detecting, assessing, reporting, and addressing information security threats. Staff must learn to spot phishing emails, understand malware and ransomware, and know how these threats spread. Crucially, they must also know the reporting procedures for suspicious activity and their role in protecting sensitive information like student and employee data.
The goal is not to make teachers cybersecurity experts, but to give them practical knowledge for daily use to keep the school safe.
Texas HB 3834 does not include direct financial penalties for non-compliance. No specific fines are written into the law.
However, non-compliance has serious consequences. The law requires periodic audits to ensure compliance. Documented failure to meet training requirements can lead to increased scrutiny from state agencies and reputational damage.
The most significant penalty is the increased vulnerability to attacks. The costs of recovering from a data breach or ransomware attack—including downtime, recovery expenses, and loss of public trust—are staggering. Documented non-compliance also creates additional liability in the event of a breach.
Compliance isn't just about following a rule; it's about protecting your students, staff, and community from real cyber threats.
Texas HB 3834 is more than a compliance requirement—it's a foundation for protecting what matters most in our schools. This legislation mandates annual cybersecurity training for employees with computer system access, creating a vital "human firewall" against the evolving landscape of cyber threats targeting educational institutions.
The law's requirements are clear: cybersecurity coordinators must complete certified training annually, while districts have flexibility in determining training for other staff. With DIR-certified programs as the standard and an August 31 compliance reporting deadline, the framework provides structure while allowing a custom approach.
True cybersecurity isn't about checking boxes. It's about creating a culture where every staff member understands they are part of the defense team. When a teacher can spot a phishing email or a substitute recognizes a social engineering attempt, that's when real protection happens.
Cyber threats are constant and sophisticated, targeting the very people dedicated to educating our children. This is why engaging, effective training that sticks is so crucial.
At CyberNut, we've seen how the right approach can transform cybersecurity from a dreaded requirement into an empowering skill. Our focus on gamified micro-trainings and low-touch, automated solutions means your busy educators can build cyber-resilience without adding stress. We understand the unique challenges of K-12 schools, from tight budgets to staff who need practical skills to protect their students and themselves.
Ready to see where your district stands against today's sophisticated phishing attacks? Get a complimentary phishing audit for your school district to assess your current vulnerabilities and identify areas for improvement.
Building a cyber-resilient culture starts with moving beyond compliance. To find how we can help transform your educators into confident cyber defenders, Explore K-12 Cybersecurity Training That Engages Staff and Students and see how CyberNut makes cybersecurity training something your staff actually looks forward to completing.

Oliver Page

Some more Insigths


Back