
Oliver Page
Case study
September 15, 2025

Going Beyond Firewalls: How to Secure Data Shared with Third-Party EdTech Vendors requires a comprehensive approach. K-12 IT directors should implement:
Essential Security Steps:
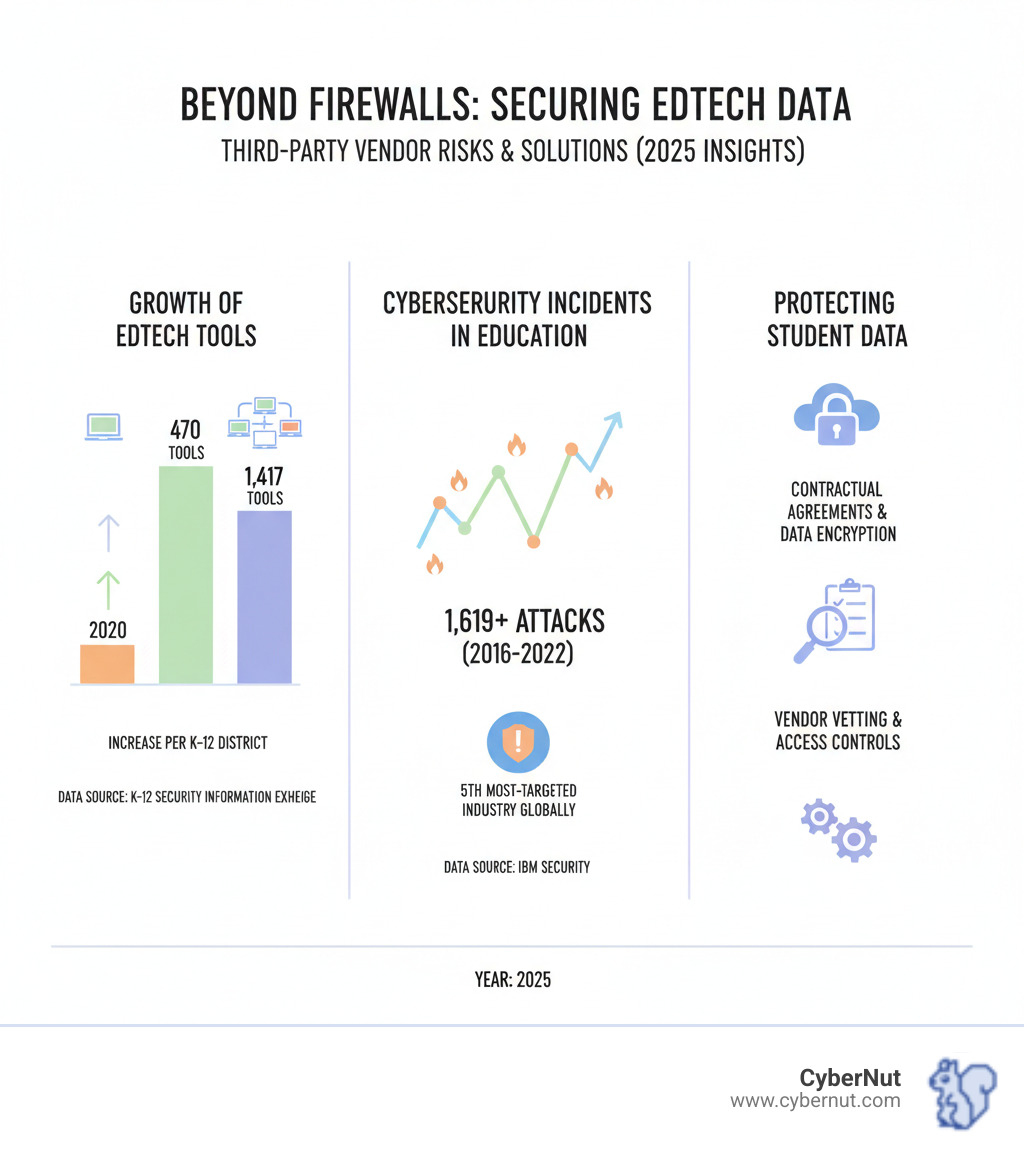
Schools now use an average of 1,417 EdTech tools annually, nearly triple the number from four years ago. A staggering 96% of these apps share student data, often without proper security.
Recent breaches paint a stark picture. The PowerSchool incident affected 62 million students, while hackers remained undetected for nine days. In New York State, human error caused 200 of the 384 student data incidents reported in 2024.
Traditional firewalls are obsolete for today's cloud-based learning. With data flowing through hundreds of third-party apps, your security perimeter extends far beyond your network.
The challenge is understanding that every new EdTech tool is a potential entry point for cybercriminals. When a breach occurs, it's not just the vendor facing consequences—your district bears the ultimate responsibility under laws like FERPA.
Cybersecurity is no longer about building a fortress-like firewall. Today's educational landscape is both exciting and terrifying.
The shift to cloud-based operations has transformed data handling. Student information, once in a school vault, is now scattered across hundreds of third-party locations. This creates an "expanding attack surface," making it critical to go Beyond Firewalls: How to Secure Data Shared with Third-Party EdTech Vendors.

The sobering reality: the education sector is now the fifth most-targeted industry in the U.S. From 2016 to 2022, researchers tracked 1,619 cyberattacks on schools.
Schools are attractive targets because they hold a goldmine of sensitive data. With the average district uses an average of 1,417 edtech tools annually, each app is a potential entry point for cybercriminals.
The types of student data at risk go beyond names and grades. EdTech vendors often collect sensitive information like home addresses, emergency contacts, academic performance records, special education documentation, health records, behavioral observations, and even psychological evaluations. A major district breach revealed that criminals accessed student psychological evaluations, medication details, and reports of abuse. This personal information can haunt families for years.
Poor data protection has devastating consequences: financial penalties, extensive federal and state investigations, and severe reputational damage. Since 2005, schools and colleges have had 3,713 data breaches, exposing 37.6 million records. Each number represents a student whose privacy was violated.
Inviting EdTech vendors into our digital world is like handing them keys to our kingdom. Understanding these vulnerabilities is crucial for securing data Beyond Firewalls: How to Secure Data Shared with Third-Party EdTech Vendors.
Network access is a major risk. Every vendor connection is a potential pathway for attackers. Granting excessive administrative privileges is even more concerning. Not following the "least privilege" principle means a single compromised vendor account could expose your entire infrastructure.
Out-of-network storage is a serious vulnerability. Vendors may copy data to their own servers with lower security standards. The 2022 Illuminate Education incident illustrates this: over 1 million student records were found on unencrypted, public databases.
Many vendors lack basic encryption. Data must be encrypted both at rest and in transit. Without it, student information is exposed. Poor access controls are another challenge; vendors need clear, audited systems for managing data access.
Perhaps the most human element is the people themselves. In New York State alone, 200 of the 384 student data incidents reported in 2024 were caused by human error. This shows that cybersecurity is only as strong as the people using it.
The risks of third-party data breaches became clear with incidents like the PowerSchool breach, which affected millions. These breaches often start with compromised vendor credentials. The lesson is that even industry leaders can have serious vulnerabilities.
Navigating student data privacy laws is a complex puzzle. K-12 leaders must understand federal and state requirements to protect students and ensure compliance.
The Family Educational Rights and Privacy Act (FERPA) is our primary federal guide. Written in 1974, it defines what student information schools can collect, store, and share, and gives parents rights over their children's records.
The Children's Internet Protection Act (CIPA) also has data privacy implications beyond content filtering, as filters alone don't protect data stored on vendor systems.
Other federal laws include the Protection of Pupil Rights Amendment (PPRA), which restricts certain student surveys, and the Individuals with Disabilities Education Act (IDEA), which requires extra privacy protections for students with disabilities.
FERPA's limitations are clear in the digital age. Written before the internet, it doesn't mandate specific cybersecurity measures. A violation only occurs after a breach, a reactive approach that leaves dangerous gaps.
The "reasonable methods" ambiguity in FERPA creates confusion. The law requires "reasonable methods" to verify data sharing and staff access, but doesn't define what is "reasonable" today, such as encryption or multi-factor authentication.
State-level laws add complexity. States like New York, California, and Texas have their own student privacy laws, some with explicit cybersecurity and breach notification rules.
The importance of understanding both federal and state student data privacy laws is paramount. While federal laws provide a baseline, state laws often add stricter requirements. This patchwork of regulations makes compliance challenging but necessary.
Traditional firewalls are outdated. They were built when data lived behind network perimeters. Today, your data is everywhere: in the cloud, on vendor servers, and flowing through hundreds of apps.
The solution is a smarter approach: Third-Party Risk Management (TPRM). It's your game plan for keeping student data safe beyond your network.
TPRM has three pillars: thorough due diligence before signing contracts, rock-solid contractual agreements, and ongoing continuous monitoring. It's like vetting a babysitter: check references, set rules, and check in regularly.
One of the most important concepts is data minimization: only share what you absolutely must. If a reading app needs to track student progress, it doesn't need their home address. This principle, from the Fair Information Practice Principle of data minimization, dramatically reduces your risk.
You'll also need to understand the Shared Responsibility Model for cloud tools. Major providers like AWS, Azure, and Google Cloud handle "security of the cloud" (infrastructure). You and your vendors are responsible for "security in the cloud" (your data and applications).
This approach becomes part of your broader Data Security and Privacy Plan, creating multiple layers of protection.
Before any vendor gets student data, they need a thorough security check-up. This is about being responsible to your students and their families.
Start with comprehensive security questionnaires. Tools like the Cloud Security Alliance's Cloud Security Matrix (CSM) and the CAIQ help you evaluate vendors against industry best practices. Ask for proof.
Review their privacy policies and terms of service. Focus on data collection practices. Do they collect only what's necessary? Choose edtech products that prioritize data minimization.
You also need to examine their encryption standards for data in transit and at rest, their access controls, and their data handling procedures. These technical details are the foundation of good security.
Here are 10 essential questions every EdTech vendor should answer:
A helpful checklist is available for download to guide this process.
After vetting a vendor, get everything in writing with a strong Data Protection Agreement (DPA). This legal safety net specifies the vendor's responsibilities and the consequences of failure.
Use frameworks like the Student Data Privacy Consortium's National Data Privacy Agreement (NDPA) or templates from organizations like the Texas Student Privacy Alliance as starting points.
Your DPA must define student data and establish that your district retains ownership. The vendor should only use data for the agreed-upon educational purpose—no selling data or commercial use. Laws like Kansas Statute 72-6314(c) prohibit these practices.
Breach notification requirements are critical. States have different rules; for example, Pennsylvania requires notification within three days to the DA and seven business days to individuals. Ensure your contract reflects your state's laws.
The agreement should mandate comprehensive training for vendor employees on FERPA, data privacy, and cybersecurity, mirroring regulations like New York's 8 NY C.R.R. Part 121, §121.6(a)(4).
Include clauses for data retention and disposal, audit rights to verify compliance, and indemnification to hold vendors liable for damages.
Finally, address subcontractor compliance—any company your vendor works with must meet the same security standards.
Many schools drop the ball after signing a contract. But securing data Beyond Firewalls requires ongoing attention. Security is a continuous process, not a one-time task.
Ongoing audits are essential. Verify vendor security standards by requesting annual updates of certifications like SOC 2 Type 2 or ISO 27001. For example, ExploreLearning's ISO 27001:2013 certification in 2024 shows the commitment you should expect.
You should also regularly reassess risk levels, especially when vendors change services or data types. Systems can conform to stricter access requirements, and you must ensure vendors keep pace.
Most importantly, have clear procedures for revoking access when contracts end or security concerns arise. You need to be able to cut ties quickly and completely.
This continuous monitoring ties back to the Shared Responsibility Model. You are responsible for ensuring your vendors uphold their end of the bargain. This moves you from reactive damage control to Proactive Cybersecurity: Safeguarding K-12 Schools from Emerging Threats.
Every vendor relationship is a trust-but-verify situation. The verification part never ends.
Even with bulletproof network security, a single click on a phishing email or an unvetted app download by a teacher can bypass all technical safeguards.

This is why a strong "human firewall" through staff education is critical for going Beyond Firewalls: How to Secure Data Shared with Third-Party EdTech Vendors. Your people are your first and last line of defense.
Shadow IT is a major challenge. A well-intentioned teacher might use a new, unvetted app for their class, unknowingly introducing an application that collects student data without proper security.
Create a culture where educators submit software requests for approval. This protects innovation, not crushes it. When teachers understand the process keeps students safe, they become security partners.
Phishing awareness deserves special attention. Today's phishing attempts look like legitimate messages from trusted vendors. When staff learn to spot red flags like urgent language or requests for login credentials, they become an early warning system.
Training on secure app usage goes beyond strong passwords. Staff need to understand multi-factor authentication, privacy settings, and what app permissions mean. An app asking for camera and microphone access for spelling practice should raise eyebrows.
Your Acceptable Use Policies (AUPs) provide the foundation, but they need to be reinforced with regular, engaging reminders about digital conduct.
Empowering educators means giving them the knowledge to make smart security decisions. When a teacher can spot a new tool with a poor privacy policy, they've become part of your security strategy.
The Cybersecurity and Infrastructure Security Agency provides free training resources available to educators, making it easier to implement comprehensive cybersecurity education.
The importance of ongoing cybersecurity education for school staff cannot be overstated. Threats evolve, and your human firewall needs regular updates. Investing in your people's security knowledge builds a culture of awareness that protects your entire school community.
Navigating EdTech security is overwhelming. Here are common questions from K-12 IT leaders about going Beyond Firewalls: How to Secure Data Shared with Third-Party EdTech Vendors.
The biggest risk is the sheer scale. With an [average of 1,417 edtech tools](https://www.prnewswire.com/news-releases/k-12-students-each-accessed-143-unique-digital-tools-during-the-2122-school-year-while-educators-interacted-with-148-new-learnplatform-report-shows-301607388.html) per district, the real danger is a lack of a standardized vetting process. When procurement happens without IT involvement, every unvetted app becomes a potential entry point, expanding your attack surface. A rigorous, consistent vetting process is critical to reduce this risk.
While a Data Protection Agreement can assign financial liability to a vendor, the district is ultimately responsible under laws like FERPA. If a vendor's negligence causes a breach, your district still faces investigations, penalties, and reputational damage. The Department of Education holds the district accountable. This is why continuous monitoring and strong vendor oversight are essential. You are the general contractor; you are responsible for your subcontractors' work.
Transparency with parents builds trust. Create a public inventory of approved EdTech tools on your district website with clear, jargon-free summaries of what data is collected and why. Provide an easy way for parents to ask questions and respond quickly. Send regular updates via newsletters or parent portals. This transparency builds trust and turns parents into allies.
Protecting student data today is a paradigm shift. As this guide shows, going Beyond Firewalls: How to Secure Data Shared with Third-Party EdTech Vendors requires a strategy that transcends traditional network security.
With districts using over 1,400 EdTech tools annually, every login is a potential entry point. Each vendor extends your security perimeter, and your responsibility extends with it.
Effective EdTech security rests on three pillars:
However, technical defenses fail without human preparation. Building a human firewall through staff education is your strongest defense. When staff understand risks like shadow IT and phishing, they become active participants in data protection.
This isn't about defense; it's about a proactive approach that embeds security and privacy into your EdTech decisions.
At CyberNut, we understand the unique challenges facing K-12 schools. We've developed cybersecurity training specifically for educational environments—engaging, practical solutions that build real cybersecurity resilience.
Ready to strengthen your district's human firewall? Take the first step with a complimentary phishing audit to identify your current vulnerabilities. Then explore our comprehensive resources for K-12 schools to find how we can help transform your staff into cybersecurity champions.
Together, we can build a safer digital learning environment where technology serves education without compromising student privacy.

Oliver Page

Some more Insigths


Back