
Oliver Page
Case study
November 10, 2025

What to Know About Georgia's Data Breach Notification Requirements for Schools means navigating two overlapping legal frameworks. Understanding both is critical for protecting student data and avoiding penalties.
Quick Answer: Key Requirements at a Glance
| Requirement | What You Need to Know |
|---|---|
| Timing | Notify "in the most expedient time possible and without unreasonable delay" |
| Who to Notify | Affected Georgia residents; if 10,000+ affected, also notify consumer reporting agencies |
| Third-Party Obligation | Must notify the school within 24 hours of finding a breach |
| Encryption Safe Harbor | No notification required if data was encrypted or redacted |
| Applicable Laws | O.C.G.A. § 10-1-912 (general breach law) + SB 89 (Student Data Privacy Act) |
| Enforcement | Georgia State Board of Education; violations may also breach FERPA |
Why This Matters for K-12 IT Directors
As a K-12 IT Director, you protect highly sensitive student data, from Social Security numbers to health records. A breach erodes parental trust and exposes students to identity theft, making compliance a top priority.
Georgia's approach is unique. The state has a general data breach notification statute (O.C.G.A. § 10-1-912) for all "data collectors," but schools also fall under the Student Data Privacy, Accessibility, and Transparency Act (SB 89). This 2015 law adds specific requirements for educational institutions and their third-party ed-tech vendors.
The challenge is that these laws don't perfectly align. SB 89 focuses on "online operators" handling K-12 student data, while the general law applies to anyone with computerized personal information. You must comply with both. The good news is that a clear understanding of the framework allows you to build procedures that protect students and ensure compliance.
What to Know About Georgia’s Data Breach Notification Requirements for Schools basics:
Georgia's legal landscape requires schools to steer two overlapping laws. First is the general data breach statute, O.C.G.A. § 10-1-912, which applies to any entity—including schools—that handles personal information of Georgia residents.
Second is the Student Data Privacy, Accessibility, and Transparency Act (O.C.G.A. §20-2-661 through 20-2-667), or SB 89. Passed in 2015, this law was created specifically for K-12 education, recognizing that student data and the vendors who handle it require special protections.
These state laws also interact with federal laws, primarily the Family Educational Rights and Privacy Act (FERPA), which protects student education records. A breach violating SB 89 could also be a FERPA violation, potentially risking a district's federal funding. Other laws like the Children's Online Privacy Protection Rule (COPPA) add further layers of compliance.
The takeaway is that your district must comply with both laws. The general statute covers basic notification mechanics, while SB 89 adds specific rules for student data and ed-tech vendors.
Not all data triggers a notification. Under the general statute (O.C.G.A. § 10-1-912), "personal information" is an individual's first name or initial and last name combined with one of the following unencrypted data elements:
Publicly available information is excluded, and the law only covers electronic data.
SB 89 uses a much broader definition. "Student personally identifiable information" (student PII) is any data that, alone or combined, can be linked to a specific student. This includes:
This broad definition recognizes that combining seemingly innocuous data points can identify a student, so it protects a wider range of information.
Under the general breach law, obligations fall on "information brokers" (entities that sell personal data) and "data collectors." A "data collector" is any entity that maintains personal information, which explicitly includes public schools and districts. Your district is a "data collector" under Georgia law.
SB 89 adds the "online operator." This refers to any third-party entity operating a website, online service, or app used for K-12 purposes that collects student PII. In short, this means your ed-tech vendors—from learning management systems to digital curriculum providers.

Critically, while your district is a "data collector," your vendors are "online operators" with their own legal duties. Your contracts must include strong data protection provisions ensuring vendors understand their obligations under SB 89, including the requirement to notify you of a breach within 24 hours.
Both your district and your vendors share responsibility for protecting student data.
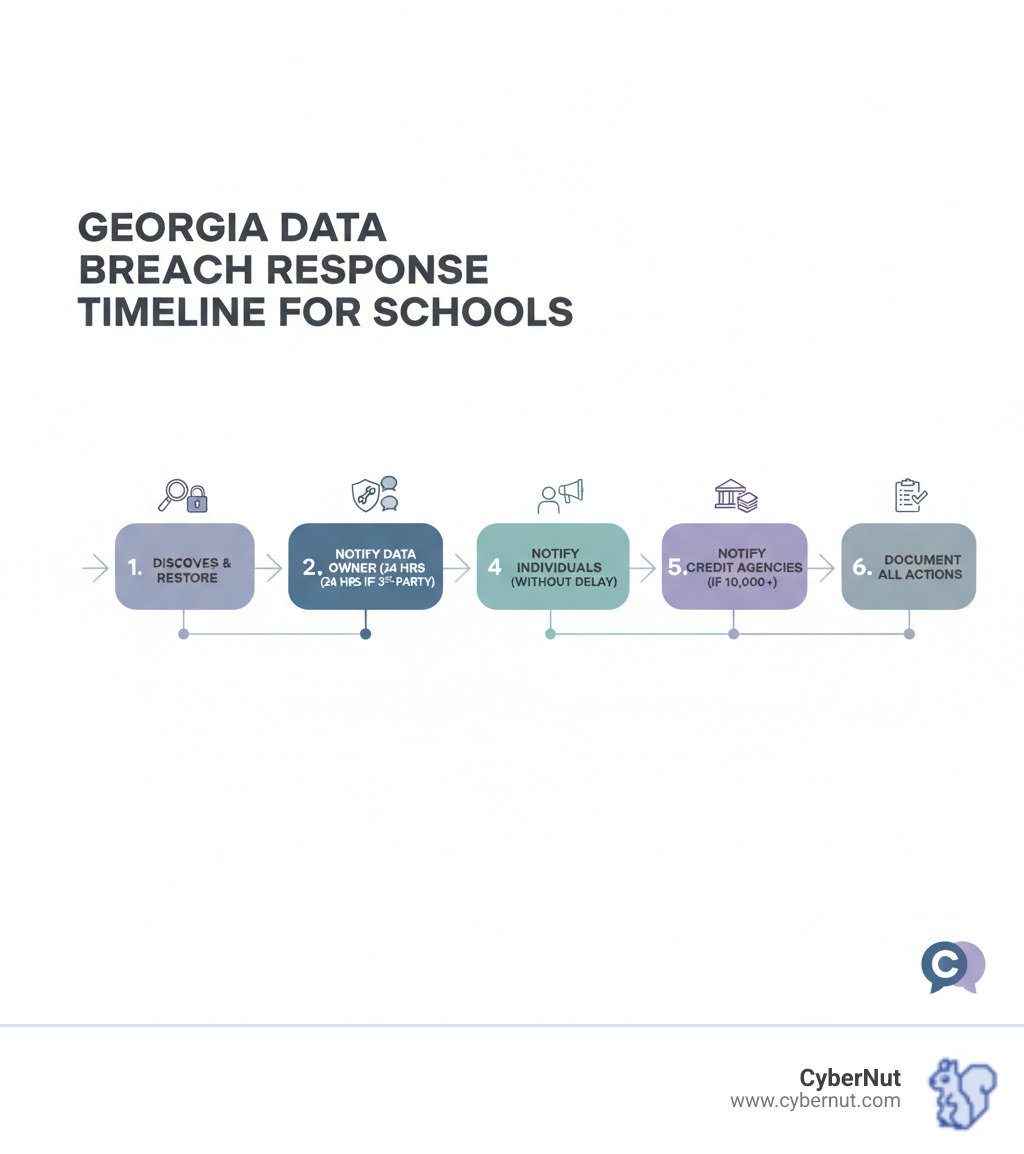
When a data breach occurs, a clear, step-by-step response is essential. Here’s how to steer Georgia's requirements when the pressure is on.
What Actually Triggers a Notification?
A notification is triggered by the unauthorized acquisition of unencrypted personal information or student PII. If someone who shouldn't have access gets the data, the clock starts ticking.
However, if the compromised data was encrypted or redacted, you may fall under a "safe harbor," meaning notification is likely not required. Encryption is your best insurance policy against the administrative burden of a breach.

Georgia law requires notification in the "most expedient time possible and without unreasonable delay." This means you must act quickly but also take the necessary time to assess the breach scope and restore system integrity. Don't let the investigation drag on, as the law expects urgency.
The 24-Hour Rule for Third Parties
If a third-party vendor experiences a breach involving your data, they must notify your school district within 24 hours of finding it. This rapid alert is critical, as it starts your own clock for notifying affected families.
Law Enforcement Coordination
Notification can be delayed if law enforcement determines it will compromise a criminal investigation. Be sure to get this request in writing.
Once you're ready to notify, you have several options for reaching affected families.
Choosing Your Notification Method
Georgia law permits:
A combination of email and phone calls is often the most effective approach.
When Direct Notification Isn't Practical
If the cost of direct notification exceeds $50,000, the affected group is larger than 100,000 people, or you lack contact information, you can use substitute notice. This requires:
What Should the Notification Say?
While the law isn't prescriptive, your notice should be clear, honest, and helpful. Include a description of the incident, the types of information involved, steps the school has taken, contact information for questions, and advice for how families can protect themselves (e.g., monitoring credit reports).
Not every incident requires external notification. Understanding these exemptions is key.
The Encryption Safe Harbor: As mentioned, if compromised data was properly encrypted and the key was not stolen, notification is generally not required.
Good-Faith Employee Access: An accidental acquisition of data by an employee for legitimate work purposes is not considered a breach, as long as the information is not used improperly or disclosed further. You should still document the incident and provide retraining.
Publicly Available Information: Data that is already lawfully available in the public domain does not trigger notification requirements.
Even if an exemption applies, you should still document the incident internally and take steps to prevent a recurrence. For more on building a comprehensive security program, explore our resources.
Accountability is the backbone of Georgia's data breach laws. Understanding the roles, responsibilities, and penalties is key to compliance and creating a culture of responsibility where everyone—from teachers to IT directors—plays a part in protecting student data.
Under SB 89, schools and vendors must implement data security training and policies. This is an organization-wide duty. Teachers must handle PII securely, and administrators must ensure policies are followed. IT directors build the secure infrastructure, but security is everyone's job. A single click on a phishing email can cause a breach, which is why effective training is so important.
SB 89 also requires the Georgia Department of Education (GaDOE) to have a Chief Privacy Officer to oversee state-level policies. While districts don't need this specific title, they must designate someone to manage data privacy compliance.

Enforcement and Penalties:
Every third-party vendor handling student data is a potential security risk. Your contracts with these "online operators" are a legal necessity and must clearly define data security and breach notification duties.
Key Vendor Requirements:
When a vendor has a breach, it's your school's reputation on the line. Choose your partners wisely.
A proactive strategy is always better than a reactive one. Building strong defenses before an incident is the smartest way to manage data security and comply with What to Know About Georgia's Data Breach Notification Requirements for Schools.
This approach combines proactive prevention with a robust Incident Response Plan (IRP) that guides your team during a crisis.
Building Your Incident Response Plan
An effective IRP is a roadmap for when stress is high. It should outline:
The Three Pillars of Data Protection
Your prevention strategy should be built on three key safeguards:
Smart Data Management
Reduce your risk by reducing your data footprint. A data retention and disposal policy should define how long student information is kept and how it's securely destroyed. Unnecessary data is a liability.
The Human Element
Most breaches start with human error, often a staff member clicking a phishing email. Cybersecurity training is therefore your most critical defense. Effective training must be regular, engaging, and specific to the threats your school faces, helping staff recognize and report suspicious activity.
To shift from reactive to proactive, build security into your school's culture:
Consider a complimentary phishing audit for your school district to understand your specific vulnerabilities. This knowledge is the first step toward building true resilience.
Navigating data breach laws can be complex. Here are concise answers to common questions about What to Know About Georgia's Data Breach Notification Requirements for Schools.
Generally, no. Georgia's laws provide an "encrypted data safe harbor." If the compromised data was encrypted and the encryption key was not also compromised, notification to individuals is typically not required. This makes encryption one of your most powerful tools for both protecting data and limiting liability.
The first priority is containment. Immediately isolate the affected systems to prevent further unauthorized access or data loss. Once contained, begin an internal investigation to determine the scope of the breach: what data was involved, how it happened, and who is affected. While investigating, take steps to restore system integrity by patching vulnerabilities and changing passwords. If a third party is involved, they must notify you within 24 hours. Document every step you take.
Yes, and they can be severe. While individuals can't sue directly for failure to notify, a violation can be deemed an "unfair or deceptive trade practice," leading to action by the state attorney general. The Georgia State Board of Education enforces the student-specific law (SB 89) and can investigate complaints. Furthermore, a violation of SB 89 could also be a FERPA violation, potentially jeopardizing your district's federal funding. Beyond legal penalties, the loss of trust with parents and the community can cause long-lasting reputational damage.
What to Know About Georgia's Data Breach Notification Requirements for Schools involves navigating a dual legal framework: the general breach statute (O.C.G.A. § 10-1-912) and the Student Data Privacy Act (SB 89). The requirements are detailed, but true protection goes beyond simple compliance.
The most effective strategy is to shift from a reactive to a proactive mindset, building a culture where cybersecurity is a shared responsibility for everyone in your district. This starts with empowering your staff, who are your first line of defense against cyberattacks like phishing.
Regular, engaging training is the key to changing your staff from potential targets into a human firewall. When your team can spot and report threats, you create a resilient defense that technology alone cannot provide.
At CyberNut, we understand the unique challenges K-12 schools face. Our cybersecurity training is designed specifically for educators: automated, gamified micro-trainings that engage staff without adding to their workload. Our low-touch approach strengthens your school's defenses efficiently and effectively.
Don't wait for a breach to test your defenses. Take a proactive step to protect your students and your school's reputation. We invite you to get a complimentary phishing audit for your school district. This free audit will reveal your vulnerabilities and provide a clear path toward improving your security posture.
Ready to build a truly cyber-aware culture? Learn more about how CyberNut can help you turn compliance into confidence and build resilient protection for your school community.

Oliver Page

Some more Insigths


Back