
Oliver Page
Case study
November 5, 2025

What to Know About FIPA: Data Protection Rules for Florida Schools starts with understanding three critical laws that protect student information. Florida schools must steer a complex web of federal and state regulations designed to keep sensitive student data secure in an increasingly digital learning environment.
As millions of students across Florida engage with digital learning platforms daily, their personal information—from Social Security numbers to online account credentials—becomes a prime target for cyber threats. Schools store everything from financial data to medical records, making educational institutions attractive targets for data breaches.
The stakes are high. Non-compliance with FIPA can result in penalties up to $500,000 per breach, while FERPA violations can lead to loss of federal funding. For K-12 IT Directors, this means balancing effective cybersecurity with limited resources and avoiding disruptions to daily school operations.
This guide breaks down what Florida schools need to know about FIPA and related data protection requirements, offering practical steps to achieve compliance while protecting students and staff from rising cyber threats.
Common What to Know About FIPA: Data Protection Rules for Florida Schools vocab:
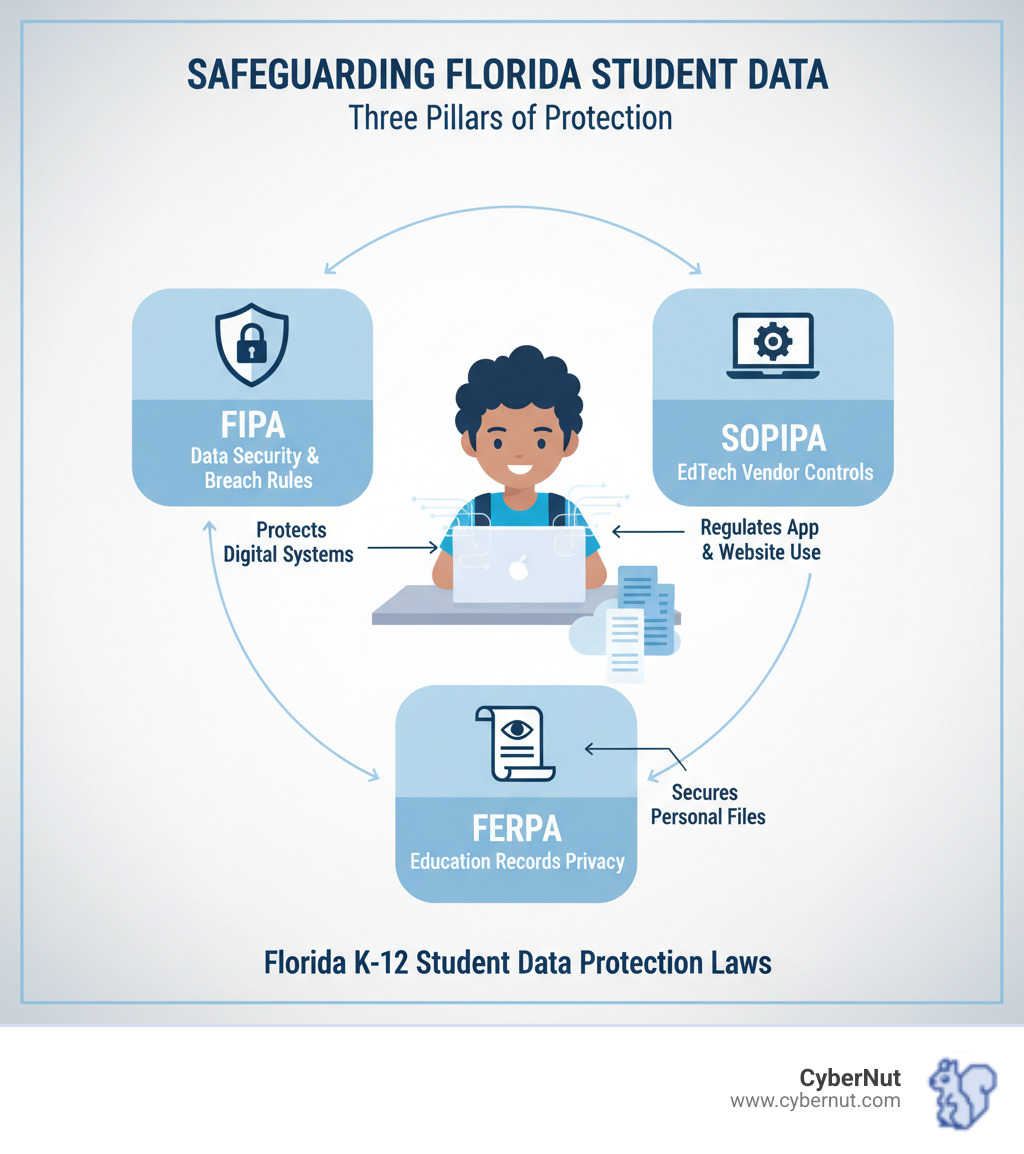
If you're managing student data in Florida, What to Know About FIPA: Data Protection Rules for Florida Schools begins with understanding this foundational law. The Florida Information Protection Act (FIPA) became effective in 2014, replacing earlier data breach notification laws with a more robust framework that continues to shape how schools protect student information today.
FIPA's purpose is straightforward: ensure that organizations handling personal information take reasonable security measures and notify affected individuals promptly when breaches occur. This isn't just about businesses—FIPA applies to Florida schools, from small private institutions to large public districts, along with any vendors they work with.
The law covers both covered entities (organizations that collect and store personal information) and third-party agents (vendors contracted to handle that data on behalf of schools). So when your district partners with a student information system provider or cloud storage service, both your school and that vendor must meet FIPA's requirements.
For a comprehensive look at this legislation's technical details, The Florida Information Protection Act (FIPA) offers valuable insights.
FIPA gets specific about what counts as personal information. It's not just about names—it's about combinations of data that could identify a student and potentially cause harm if exposed.
Under FIPA, personal information means a student's first name (or first initial) and last name combined with one or more of these unencrypted data elements:
Social Security numbers remain one of the most sensitive identifiers schools handle, especially for financial aid or employment records. Driver's license numbers or state ID numbers also qualify, which matters for older students and staff records.
Financial account data includes account numbers, credit or debit card information, or any security codes that could grant access to someone's financial accounts. This becomes relevant when schools process lunch payments, collect fees, or manage payroll.
Schools also handle medical information about students' health histories and treatments, plus health insurance information like policy numbers. These records require extra care under FIPA's definition.
Here's a modern addition that catches many schools off guard: online account credentials. This means a username or email address combined with a password or security question that would open up an online account. With so many digital learning platforms in use today, this provision significantly expands what schools must protect.
There's good news though. FIPA includes an encrypted data exemption—personal information that's properly encrypted, secured, or modified so it's unusable if breached generally doesn't trigger the same notification requirements. This makes encryption one of your strongest tools for compliance.
FIPA's reach is intentionally broad. The law defines covered entities as any commercial entity—whether a sole proprietorship, corporation, partnership, or other business structure—that acquires, maintains, stores, or uses personal information of Florida residents. Importantly, this definition explicitly includes governmental entities, which means public school districts fall squarely within FIPA's scope.
Third-party agents face the same obligations. These are vendors contracted to maintain, store, or process personal information on behalf of a covered entity. When your school outsources its student information system, contracts with a learning management platform, or uses cloud-based services for data storage, those vendors become third-party agents under FIPA.
What this means for K-12 schools: Both public and private Florida schools must comply, regardless of size. Your contracted service providers must also meet FIPA's standards. Even if a vendor operates outside Florida, they're subject to FIPA when handling Florida students' data.
While FIPA casts a wide net, it recognizes that not every situation demands the same response. Understanding these exemptions helps schools focus their compliance efforts where they matter most.
Encrypted or secured data receives the most significant exemption. When you've properly encrypted sensitive information so it's unreadable without the decryption key, FIPA's breach notification requirements may not apply even if that encrypted data is accessed without authorization. This creates a powerful incentive for schools to implement strong encryption across all systems storing personal information.
De-identified information that's been stripped of personally identifiable elements and can't be traced back to specific students falls outside FIPA's breach notification requirements. However, true de-identification requires careful attention—simply removing names isn't enough if other data points could still identify individuals.
Law enforcement investigations sometimes necessitate delays in breach notifications. If authorities determine that notifying affected individuals would impede an active criminal investigation, FIPA allows covered entities to postpone notification until law enforcement gives the green light.
Schools already compliant with certain federal laws like HIPAA or GLBA may find some overlap in requirements. While K-12 schools typically aren't HIPAA-covered entities, understanding how these federal frameworks interact with FIPA helps when working with school nurses or financial service providers who do fall under those regulations.
The key takeaway? Don't assume an exemption applies without careful analysis. When in doubt, treating data as if it requires full FIPA protection is the safer approach—and consulting legal counsel ensures you're making informed decisions about your school's compliance strategy.
At its heart, FIPA asks two fundamental things of Florida schools: protect the data you hold and tell people promptly when something goes wrong. These aren't just bureaucratic boxes to check—they're essential safeguards for the thousands of students and staff whose personal information schools manage every day. For a comprehensive look at protecting educational data, explore resources on Cybersecurity for Educational Institutions.
FIPA doesn't hand you a 500-page technical manual and say "follow this exactly." Instead, it requires covered entities—including Florida schools—to take "reasonable measures" to protect electronic data containing personal information. Think of it as a flexible, common-sense approach that scales with your school's size and the sensitivity of the data you're protecting.
What does "reasonable" actually mean? It's about implementing physical, administrative, and technological safeguards that match the risk. For a small private school, this might look different than for a large district with tens of thousands of students, but the principle remains the same: protect what matters.
In practical terms, reasonable measures typically include limiting access to sensitive data based on job roles (your cafeteria staff probably don't need access to Social Security numbers), encrypting data both when it's sitting on your servers and when it's traveling across networks, and keeping your software updated to patch security holes before they become problems. It also means training your staff to recognize phishing emails and handle data properly—because the best firewall in the world won't help if someone clicks a malicious link.
Don't forget the physical world either. Servers and devices storing personal information need to be physically secured, not sitting in an open uped closet where anyone can access them.
But data protection doesn't end when information is actively in use. FIPA also requires reasonable measures for secure disposal when records are no longer needed. Old student files can't just go in the regular trash. Physical documents need shredding, electronic media needs proper wiping that prevents recovery, and sometimes data needs to be de-identified so it can no longer be traced back to individuals.
Having a comprehensive Data Security and Privacy Plan isn't just good practice—it's your roadmap for meeting these FIPA requirements systematically.
Here's where FIPA gets serious: breach notification requirements. Understanding What to Know About FIPA: Data Protection Rules for Florida Schools means knowing exactly what to do when unauthorized access happens—because in today's threat landscape, it's often a matter of "when" rather than "if."
FIPA defines a "breach of security" as unauthorized access to electronic data that compromises the security, confidentiality, or integrity of personal information. This specifically applies when that information wasn't encrypted or properly secured. The moment your school determines a breach has occurred, you're on the clock.
The law is crystal clear: you must notify each affected Florida resident within 30 days of determining a breach occurred. That's 30 calendar days, not business days, and it starts from when you reasonably determine there was a breach—not when you first suspect something might be wrong.
Can't make the deadline? FIPA provides a narrow escape hatch: you can request an additional 15-day extension, but only for "good cause." This isn't automatic. You must notify the Florida Department of Legal Affairs in writing within that initial 30-day window, explaining why you need more time and when you'll complete the notifications.
The notification you send to affected individuals needs to be thorough. It should describe what happened, what types of personal information were involved, what you're doing about it, who they can contact for more information, and most importantly, what steps they can take to protect themselves (like placing fraud alerts or monitoring their accounts).
When breaches affect larger numbers of people, FIPA adds extra notification requirements. These tiered requirements recognize that bigger breaches have broader impacts and need more oversight.
If a breach affects 500 or more Florida residents, you're not just notifying the individuals—you're also notifying the Florida Department of Legal Affairs. This notification must happen within that same 30-day window. State authorities need to know about significant incidents so they can monitor the situation and take appropriate action if needed.
When the number climbs to 1,000 or more individuals, there's one more notification requirement: you must alert the nationwide consumer credit reporting agencies without unreasonable delay. This helps ensure affected individuals can be warned about potential credit fraud and take protective steps like credit freezes or fraud alerts.
These escalating requirements make sense when you think about it. A breach affecting 50 students is serious, but a breach affecting 5,000 students and staff requires a coordinated response involving state authorities and credit monitoring services.
It's worth noting that while schools primarily focus on student data, breaches can also affect staff members and parents whose information you maintain. A payroll system breach or a compromised parent portal could quickly push you into these higher notification thresholds.
If individuals believe their data privacy rights have been violated, they can also file a complaint with the Florida Department of Agriculture and Consumer Services, which serves as the state's consumer complaint clearinghouse.
Let's talk about the consequences, because FIPA has real teeth. Violations aren't treated as minor administrative hiccups—they're considered unfair and deceptive trade practices under Florida law. This gives the Florida Department of Legal Affairs broad authority to investigate, issue cease and desist orders, and impose substantial civil penalties.
The penalty structure is designed to encourage swift action. For the first 30 days of any violation (like failing to provide timely notice), you're looking at up to $1,000 per day. That alone adds up quickly.
But it gets steeper. After those initial 30 days, the fines jump dramatically to $50,000 for each subsequent 30-day period (or portion thereof) of continued non-compliance. These escalating fines can continue for up to 180 days. Do the math, and you'll see how quickly this becomes financially devastating.
The maximum civil penalty for a single breach can reach $500,000. That's per breach, meaning multiple distinct security incidents could result in multiple maximum penalties stacking up.
For most K-12 schools operating on tight budgets, even a fraction of these penalties would be catastrophic. But the financial cost is only part of the story. Non-compliance severely damages your school's reputation, erodes trust with parents and the community, and can lead to additional legal complications. Parents entrust you with their children's most sensitive information—losing that trust is sometimes harder to recover from than the financial penalties.
The good news? These penalties are entirely avoidable. With proper security measures, staff training, and an incident response plan, Florida schools can protect themselves from both breaches and the penalties that follow non-compliance. Understanding What to Know About FIPA: Data Protection Rules for Florida Schools is your first line of defense. Want to assess your school's vulnerability to one of the most common breach vectors? Consider a complimentary phishing audit to see where your risks lie.
Picture this: You're a K-12 IT Director in Florida, and you're trying to keep track of which law applies to which piece of student data. It's a bit like juggling—except the balls are labeled with different acronyms, and dropping one could mean serious consequences for your school.
The truth is, What to Know About FIPA: Data Protection Rules for Florida Schools isn't just about understanding one law. It's about navigating a web of federal and state regulations that often overlap, sometimes contradict, and always demand attention. FIPA sets the baseline for protecting personal information of all Florida residents, including students. But it doesn't work alone.
Schools must also contend with federal laws like FERPA and Florida's own K-12-specific SOPIPA. Each has its own scope, requirements, and enforcement mechanisms. The practical result? Schools often need to meet the highest standard required by any of these laws—whichever one is strictest in a given situation.
This gets even more complicated with the explosion of educational technology. Every new app, platform, or online service your school adopts becomes another potential point of vulnerability—and another vendor relationship you need to manage carefully. Strong vendor contracts aren't just good practice; they're essential for compliance.
For a comprehensive look at how federal law fits into this picture, explore All About FERPA: The Federal Student Privacy Law That Still Matters in 2025.
Here's where things get interesting. The Family Educational Rights and Privacy Act (FERPA) has been protecting student education records since 1974—long before anyone imagined students would be logging into Chromebooks or taking tests on tablets. It's a federal law that applies to any school receiving federal funds, which means virtually every public school and most private schools in Florida.
FIPA, on the other hand, arrived in 2014 as Florida's answer to the growing threat of data breaches. It's a state law focused on protecting personal information and ensuring that when breaches happen, people get notified quickly.
Both laws aim to protect personal information, but they approach the problem from different angles. FERPA zeroes in on "education records"—basically any record a school maintains that contains information directly related to a student. This includes grades, disciplinary records, health information kept by the school nurse, and even emails about a specific student.
FIPA casts a wider net. It protects "personal information" of all Florida residents, not just students. This means Social Security numbers, driver's license numbers, financial account details, medical information, health insurance data, and online account credentials—whenever these are combined with a person's name.
The key difference? FERPA is about access and disclosure—who can see education records and under what circumstances. It gives parents (and students over 18) the right to review and request changes to those records. FIPA is about security and breach notification—how you protect data and what you do when something goes wrong.
In practice, Florida schools need to comply with both. If student data is breached, FIPA dictates your notification timeline and procedures. FERPA governs who had legitimate access to that data in the first place and what rights parents have regarding the records.
The good news? Complying with the stricter requirements of FIPA often means you're also meeting FERPA's expectations. Strong encryption, access controls, and incident response plans help you satisfy both laws simultaneously.
For more detailed information on FERPA's requirements, visit FERPA | Protecting Student Privacy.
Just when you thought you had FIPA and FERPA figured out, along comes SOPIPA—Florida's answer to the specific challenges posed by educational technology vendors.
Officially known as Senate Bill 662, SOPIPA was enacted to address a growing concern: EdTech companies were collecting massive amounts of student data through their platforms, and there weren't clear rules about what they could and couldn't do with that information. Could they use student data to target ads? Could they sell it to third parties? Could they build profiles of students for purposes unrelated to education?
SOPIPA said: Not anymore.
This law specifically targets "operators"—meaning any person or entity that operates a website, online service, online application, or mobile application that's designed and marketed primarily for K-12 school purposes. If your school uses it for educational activities, and the vendor knows it's being used in a K-12 context, SOPIPA applies.
The law defines "covered information" broadly to include personally identifiable information, materials created by students, and information about student use of the operator's site or service. Essentially, if it relates to a K-12 student and flows through an EdTech platform, it's covered.
For a deeper dive into Florida's comprehensive approach to student data privacy, check out All About Florida's Student Data Privacy Act (FS 1002.222).
SOPIPA doesn't just ask EdTech vendors to be careful with student data—it explicitly tells them what they cannot do and what they must do. For schools, understanding these rules is crucial when selecting and contracting with vendors.
What EdTech Vendors Cannot Do:
SOPIPA prohibits operators from using covered information to engage in targeted advertising to students or their parents based on any information the operator has acquired through the provision of services to a K-12 school. This means no personalized ads following students around the internet based on what they did in a learning app.
Vendors also cannot create profiles of K-12 students for purposes other than supporting authorized educational or school purposes. So if a vendor wants to build a marketing profile or sell aggregated student behavior data for commercial purposes unrelated to education, that's off the table.
Perhaps most importantly, EdTech vendors are flatly prohibited from selling or renting student information. This includes selling it to data brokers, advertisers, or any other third party. Student data is not a commodity.
What EdTech Vendors Must Do:
On the flip side, SOPIPA requires operators to implement and maintain reasonable security procedures and practices appropriate to the nature of the covered information they hold. This aligns with FIPA's broader requirement for reasonable data security, but it's specifically custom to the EdTech context.
Vendors must also practice data minimization—collecting only the information necessary to provide their educational services. No hoovering up extra data "just in case."
Finally, SOPIPA gives schools and parents a powerful tool: the right to request deletion of covered information. When a school or parent asks an operator to delete a student's data (and the school is no longer using the service), the vendor must comply. This ensures that student information doesn't linger indefinitely in vendor databases.
For Florida schools, this means your vendor contracts need to explicitly address SOPIPA compliance. Before signing on the dotted line with any EdTech provider, verify that their privacy policies and data practices align with these prohibitions and requirements. Ask for written confirmation. Make it part of your procurement process.
Because at the end of the day, even if the vendor is responsible for SOPIPA compliance, a breach or misuse of student data still reflects on your school and erodes the trust parents place in you to keep their children safe online.

Oliver Page

Some more Insigths


Back